Is this not what you were looking for? Switch to the current version or choose one from the drop-down menu.
3 Authentication
Overview
In Administration → Authentication the user authentication method to Zabbix can be changed. The available methods are internal, LDAP and HTTP authentication.
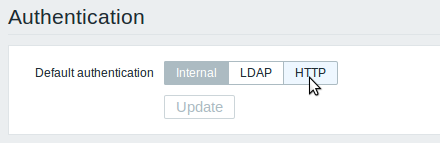
By default, internal Zabbix authentication is used. To change, click on the button with the method name and press Update.
Internal
Internal Zabbix authentication is used.
LDAP
External LDAP authentication can be used to check user names and passwords. Note that a user must exist in Zabbix as well, however its Zabbix password will not be used.
Zabbix LDAP authentication works at least with Microsoft Active Directory and OpenLDAP.
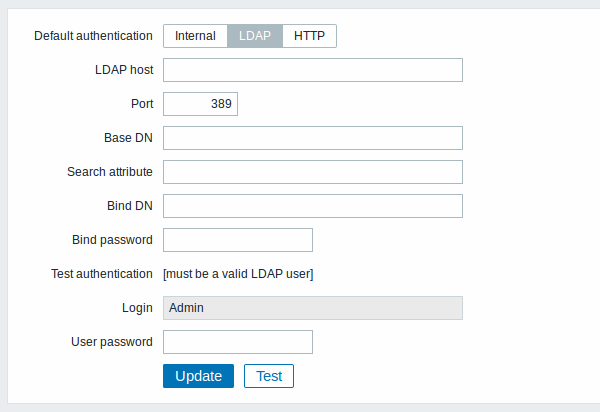
Configuration parameters:
| Parameter | Description |
|---|---|
| LDAP host | Name of LDAP server. For example: ldap://ldap.zabbix.com For secure LDAP server use ldaps protocol. ldaps://ldap.zabbix.com With OpenLDAP 2.x.x and later, a full LDAP URI of the form ldap://hostname:port or ldaps://hostname:port may be used. |
| Port | Port of LDAP server. Default is 389. For secure LDAP connection port number is normally 636. Not used when using full LDAP URIs. |
| Base DN | Base path to search accounts: ou=Users,ou=system (for OpenLDAP), DC=company,DC=com (for Microsoft Active Directory) |
| Search attribute | LDAP account attribute used for search: uid (for OpenLDAP), sAMAccountName (for Microsoft Active Directory) |
| Bind DN | LDAP account for binding and searching over the LDAP server, examples: uid=ldap_search,ou=system (for OpenLDAP), CN=ldap_search,OU=user_group,DC=company,DC=com (for Microsoft Active Directory) Required, anonymous binding is not supported. |
| Bind password | LDAP password of the account for binding and searching over the LDAP server. |
| Test authentication | Header of a section for testing |
| Login | Name of a test user (which is currently logged in the Zabbix frontend). This user name must exist in the LDAP server. Zabbix will not activate LDAP authentication if it is unable to authenticate the test user. |
| User password | LDAP password of the test user. |
In case of trouble with certificates, to make a secure LDAP connection (ldaps) work you may need to add a TLS_REQCERT allow line to the /etc/openldap/ldap.conf configuration file. It may decrease the security of connection to the LDAP catalog.
It is recommended to create a separate LDAP account (Bind DN) to perform binding and searching over the LDAP server with minimal privileges in the LDAP instead of using real user accounts (used for logging in the Zabbix frontend).
Such an approach provides more security and does not require changing the Bind password when the user changes his own password in the LDAP server.
In the table above it's ldap_search account name.
Some user groups can still be authenticated by Zabbix. These groups must have frontend access set to Internal.
HTTP
Apache-based (HTTP) authentication can be used to check user names and passwords. Note that a user must exist in Zabbix as well, however its Zabbix password will not be used.
Be careful! Make sure that Apache authentication is configured and works properly before switching it on.
In case of Apache authentication all users (even with frontend access set to Internal) will be authenticated by Apache, not by Zabbix!


