2 LDAP
Overview
External LDAP authentication can be used to check user names and passwords.
Zabbix LDAP authentication works at least with Microsoft Active Directory and OpenLDAP.
If only LDAP sign-in is configured, then the user must also exist in Zabbix, however, its Zabbix password will not be used. If authentication is successful, then Zabbix will match a local username with the username attribute returned by LDAP.
User provisioning
It is possible to configure JIT (just-in-time) user provisioning for LDAP users. In this case, it is not required that a user already exists in Zabbix. The user account can be created when the user logs into Zabbix for the first time.
When an LDAP user enters their LDAP login and password, Zabbix checks the default LDAP server if this user exists. If the user exists and does not have an account in Zabbix yet, a new user is created in Zabbix and the user is able to log in.
If JIT provisioning is enabled, a user group for deprovisioned users must be specified in the Authentication tab.
JIT provisioning also allows to update provisioned user accounts based on changes in LDAP.
LDAP JIT provisioning is available only when LDAP is configured to use "anonymous" or "special user" for binding. For direct user binding, provisioning will be made only for user login action, because logging in user password is used for such type of binding.
Multiple servers
Several LDAP servers can be defined, if necessary. For example, a different server can be used to authenticate a different user group. Once LDAP servers are configured, in user group configuration it becomes possible to select the required LDAP server for the respective user group.
If a user is in multiple user groups and multiple LDAP servers, the first server in the list of LDAP servers sorted by name in ascending order will be used for authentication.
Configuration
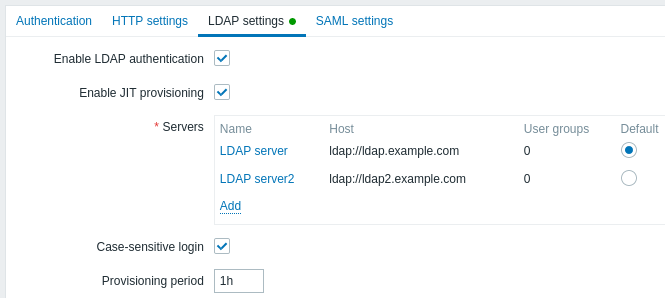
Configuration parameters:
| Parameter | Description |
|---|---|
| Enable LDAP authentication | Mark the checkbox to enable LDAP authentication. |
| Enable JIT provisioning | Mark the checkbox to enable JIT provisioning. |
| Servers | Click on Add to configure an LDAP server (see LDAP server configuration below). |
| Case-sensitive login | Unmark the checkbox to disable case-sensitive login (enabled by default) for usernames. E.g. disable case-sensitive login and log in with, for example, 'ADMIN' user even if the Zabbix user is 'Admin'. Note that with case-sensitive login disabled the login will be denied if multiple users exist in Zabbix database with similar usernames (e.g. Admin, admin). |
| Provisioning period | Set the provisioning period, i.e. how often user provisioning is performed. |
LDAP server configuration
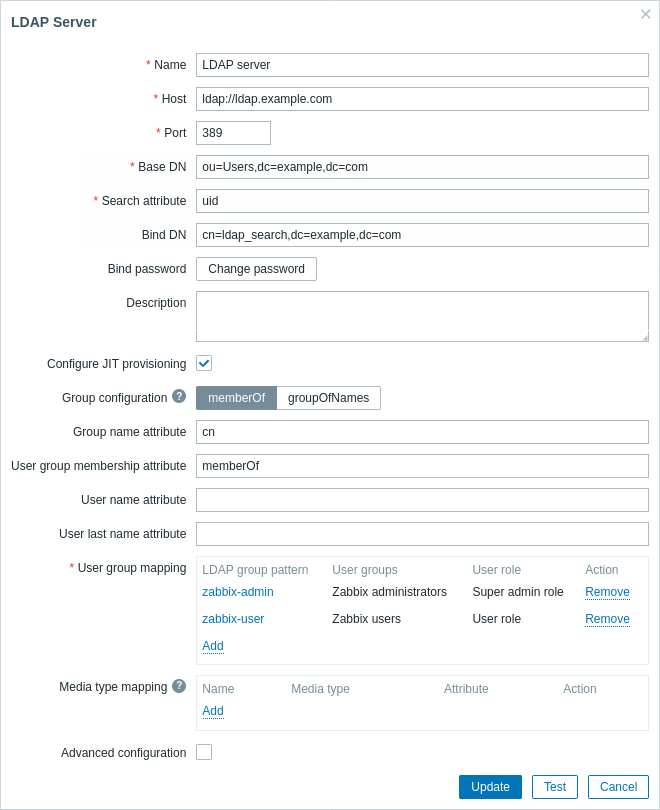
LDAP server configuration parameters:
| Parameter | Description |
|---|---|
| Name | Name of the LDAP server in Zabbix configuration. |
| Host | Host of the LDAP server. For example: ldap://ldap.example.com For secure LDAP server use ldaps protocol. ldaps://ldap.example.com With OpenLDAP 2.x.x and later, a full LDAP URI of the form ldap://hostname:port or ldaps://hostname:port may be used. |
| Port | Port of the LDAP server. Default is 389. For secure LDAP connection port number is normally 636. Not used when using full LDAP URIs. |
| Base DN | Base path to user accounts in LDAP server: ou=Users,ou=system (for OpenLDAP), DC=company,DC=com (for Microsoft Active Directory) |
| Search attribute | LDAP account attribute used for search: uid (for OpenLDAP), sAMAccountName (for Microsoft Active Directory) |
| Bind DN | LDAP account for binding and searching over the LDAP server, examples: uid=ldap_search,ou=system (for OpenLDAP), CN=ldap_search,OU=user_group,DC=company,DC=com (for Microsoft Active Directory) Anonymous binding is also supported. Note that anonymous binding potentially opens up domain configuration to unauthorized users (information about users, computers, servers, groups, services, etc.). For security reasons, disable anonymous binds on LDAP hosts and use authenticated access instead. |
| Bind password | LDAP password of the account for binding and searching over the LDAP server. |
| Description | Description of the LDAP server. |
| Configure JIT provisioning | Mark this checkbox to show options related to JIT provisioning. |
| Group configuration | Select the group configuration method: memberOf - by searching users and their group membership attribute groupOfNames - by searching groups through the member attribute Note that memberOf is preferable as it is faster; use groupOfNames if your LDAP server does not support memberOf or group filtering is required. |
| Group name attribute | Specify the attribute to get the group name from all objects in the memberOf attribute (see the User group membership attribute field)The group name is necessary for user group mapping. |
| User group membership attribute | Specify the attribute that contains information about the groups that the user belongs to (e.g. memberOf).For example, the memberOf attribute may hold information like this: memberOf=cn=zabbix-admin,ou=Groups,dc=example,dc=comThis field is available only for the memberOf method. |
| User name attribute | Specify the attribute that contains the user's first name. |
| User last name attribute | Specify the attribute that contains the user's last name. |
| User group mapping | Map an LDAP user group pattern to Zabbix user group and user role. This is required to determine what user group/role the provisioned user will get in Zabbix. Click on Add to add a mapping. The LDAP group pattern field supports wildcards. The group name must match an existing group. If an LDAP user matches several Zabbix user groups, the user becomes a member of all of them. If a user matches several Zabbix user roles, the user will get the one with the highest permission level among them. |
| Media type mapping | Map the user's LDAP media attributes (e.g. email) to Zabbix user media for sending notifications. |
| Advanced configuration | Mark this checkbox to show advanced configuration options (see below). |
| StartTLS | Mark the checkbox to use the StartTLS operation when connecting to LDAP server. The connection will fall if the server doesn't support StartTLS. StartTLS cannot be used with servers that use the ldaps protocol. |
| Search filter | Define a custom string when authenticating user in LDAP. The following placeholders are supported:%{attr} - search attribute name (uid, sAMAccountName)%{user} - user username value to authenticate.If omitted then LDAP will use the default filter: (%{attr}=%{user}). |
The following fields are specific to "groupOfNames" as the Group configuration method:
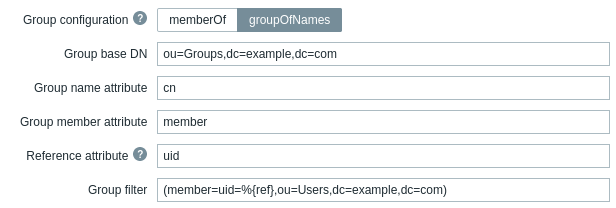
| Parameter | Description |
|---|---|
| Group base DN | Base path to the groups in LDAP server. |
| Group name attribute | Specify the attribute to get the group name in the specified base path to groups. The group name is necessary for user group mapping. |
| Group member attribute | Specify the attribute that contains information about the members of the group in LDAP (e.g. member). |
| Reference attribute | Specify the reference attribute for the group filter (see the Group filter field). Then use %{ref} in the group filter to get values for the attribute specified here. |
| Group filter | Specify the filter to retrieve the group that the user is member of. For example, (member=uid=%{ref},ou=Users,dc=example,dc=com) will match "User1" if the member attribute of the group is uid=User1,ou=Users,dc=example,dc=com and will return the group that "User1" is a member of. |
In case of trouble with certificates, to make a secure LDAP connection (ldaps) work you may need to add a TLS_REQCERT allow line to the /etc/openldap/ldap.conf configuration file. It may decrease the security of connection to the LDAP catalog.
It is recommended to create a separate LDAP account (Bind DN) to perform binding and searching over the LDAP server with minimal privileges in the LDAP instead of using real user accounts (used for logging in the Zabbix frontend).
Such an approach provides more security and does not require changing the Bind password when the user changes his own password in the LDAP server.
In the table above it's the ldap_search account name.
Testing access
The Test button allows to test user access:
| Parameter | Description |
|---|---|
| Login | LDAP user name to test (prefilled with the current user name from Zabbix frontend). This user name must exist in the LDAP server. Zabbix will not activate LDAP authentication if it is unable to authenticate the test user. |
| User password | LDAP user password to test. |

