Is this not what you were looking for? Switch to the current version or choose one from the drop-down menu.
- Best practices for secure Zabbix setup
- Overview
- Principle of least privilege
- Secure user for Zabbix agent
- UTF-8 encoding
- Revoke write access to SSL configuration (Windows)
- Setting up SSL for Zabbix frontend
- Enabling Zabbix on root directory of URL
- Enabling HTTP Strict Transport Security (HSTS) on the web server
- Disabling web server information exposure
- Disabling default web server error pages
- Removing web server test page
- Zabbix settings
- Zabbix Windows agent with OpenSSL
- Security vulnerabilities
Best practices for secure Zabbix setup
Overview
This section contains best practices that should be observed in order to set up Zabbix in a secure way.
The practices contained here are not required for the functioning of Zabbix. They are recommended for better security of the system.
Principle of least privilege
The principle of least privilege should be used at all times for Zabbix. This principle means that user accounts (in Zabbix frontend) or process user (for Zabbix server/proxy or agent) have only those privileges that are essential to perform intended functions. In other words, user accounts at all times should run with as few privileges as possible.
Giving extra permissions to 'zabbix' user will allow it to access configuration files and execute operations that can compromise the overall security of the infrastructure.
When implementing the least privilege principle for user accounts, Zabbix frontend user types should be taken into account. It is important to understand that while a "Admin" user type has less privileges than "Super Admin" user type, it has administrative permissions that allow managing configuration and execute custom scripts.
Some information is available even for non-privileged users. For example, while Administration → Scripts is not available for non-Super Admins, scripts themselves are available for retrieval by using Zabbix API. Limiting script permissions and not adding sensitive information (like access credentials, etc) should be used to avoid exposure of sensitive information available in global scripts.
Secure user for Zabbix agent
In the default configuration, Zabbix server and Zabbix agent processes share one 'zabbix' user. If you wish to make sure that the agent cannot access sensitive details in server configuration (e.g. database login information), the agent should be run as a different user:
- Create a secure user
- Specify this user in the agent configuration file ('User' parameter)
- Restart the agent with administrator privileges. Privileges will be dropped to the specified user.
UTF-8 encoding
UTF-8 is the only encoding supported by Zabbix. It is known to work without any security flaws. Users should be aware that there are known security issues if using some of the other encodings.
Revoke write access to SSL configuration (Windows)
If you have compiled Zabbix agent on Windows, with OpenSSL located in an unprotected directory (e.g., c:\openssl-64bit, C:\OpenSSL-Win64-111-static, or C:\dev\openssl), make sure to revoke write access from non-administrator users to this directory. Otherwise, the agent loads SSL settings from a path that can be modified by unprivileged users, resulting in a potential security vulnerability.
Setting up SSL for Zabbix frontend
On RHEL/Centos, install mod_ssl package:
Create directory for SSL keys:
Create SSL certificate:
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/httpd/ssl/private/apache-selfsigned.key -out /etc/httpd/ssl/apache-selfsigned.crtFill out the prompts appropriately. The most important line is the one that requests the Common Name. You need to enter the domain name that you want to be associated with your server. You can enter the public IP address instead if you do not have a domain name. We will use example.com in this article.
Country Name (2 letter code) [XX]:
State or Province Name (full name) []:
Locality Name (eg, city) [Default City]:
Organization Name (eg, company) [Default Company Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:example.com
Email Address []:Edit Apache SSL configuration:
/etc/httpd/conf.d/ssl.conf
DocumentRoot "/usr/share/zabbix"
ServerName example.com:443
SSLCertificateFile /etc/httpd/ssl/apache-selfsigned.crt
SSLCertificateKeyFile /etc/httpd/ssl/private/apache-selfsigned.keyRestart the Apache service to apply the changes:
Enabling Zabbix on root directory of URL
Add a virtual host to Apache configuration and set permanent redirect for document root to Zabbix SSL URL. Do not forget to replace example.com with the actual name of the server.
/etc/httpd/conf/httpd.conf
#Add lines
<VirtualHost *:*>
ServerName example.com
Redirect permanent / https://example.com
</VirtualHost>Restart the Apache service to apply the changes:
Enabling HTTP Strict Transport Security (HSTS) on the web server
To protect Zabbix frontend against protocol downgrade attacks, we recommend to enable HSTS policy on the web server.
For example, to enable HSTS policy for your Zabbix frontend in Apache configuration:
add the following directive to your virtual host's configuration:
Restart the Apache service to apply the changes:
Disabling web server information exposure
It is recommended to disable all web server signatures as part of the web server hardening process. The web server is exposing software signature by default:
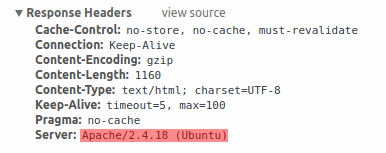
The signature can be disabled by adding two lines to the Apache (used as an example) configuration file:
PHP signature (X-Powered-By HTTP header) can be disabled by changing the php.ini configuration file (signature is disabled by default):
Web server restart is required for configuration file changes to be applied.
Additional security level can be achieved by using the mod_security (package libapache2-mod-security2) with Apache. mod_security allows to remove server signature instead of only removing version from server signature. Signature can be altered to any value by changing "SecServerSignature" to any desired value after installing mod_security.
Please refer to documentation of your web server to find help on how to remove/change software signatures.
Disabling default web server error pages
It is recommended to disable default error pages to avoid information exposure. Web server is using built-in error pages by default:
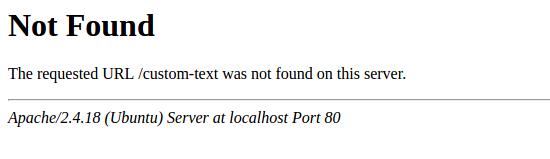
Default error pages should be replaced/removed as part of the web server hardening process. The "ErrorDocument" directive can be used to define a custom error page/text for Apache web server (used as an example).
Please refer to documentation of your web server to find help on how to replace/remove default error pages.
Removing web server test page
It is recommended to remove the web server test page to avoid information exposure. By default, web server webroot contains a test page called index.html (Apache2 on Ubuntu is used as an example):
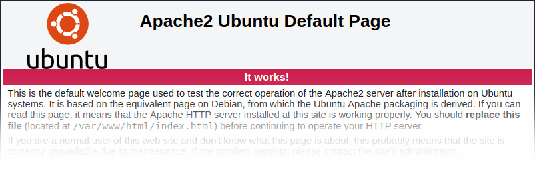
The test page should be removed or should be made unavailable as part of the web server hardening process.
Zabbix settings
By default, Zabbix is configured with X-Frame-Options HTTP response header set to SAMEORIGIN, meaning that content can only be loaded in a frame that has the same origin as the page itself.
Zabbix frontend elements that pull content from external URLs (namely, the URL dashboard widget) display retrieved content in a sandbox with all sandboxing restrictions enabled.
These settings enhance the security of the Zabbix frontend and provide protection against XSS and clickjacking attacks. Super Admins can modify iframe sandboxing and X-Frame-Options HTTP response header parameters as needed. Please carefully weigh the risks and benefits before changing default settings. Turning sandboxing or X-Frame-Options off completely is not recommended.
Zabbix Windows agent with OpenSSL
Zabbix Windows agent compiled with OpenSSL will try to reach the SSL configuration file in c:\openssl-64bit. The "openssl-64bit" directory on disk C: can be created by non-privileged users.
So for security hardening, it is required to create this directory manually and revoke write access from non-admin users.
Please note that the directory names will be different on 32-bit and 64-bit versions of Windows.
Security vulnerabilities
CVE-2021-42550
In Zabbix Java gateway with logback version 1.2.7 and prior versions, an attacker with the required privileges to edit configuration files could craft a malicious configuration allowing to execute arbitrary code loaded from LDAP servers.
Vulnerability to CVE-2021-42550 has been fixed since Zabbix 5.4.9. However, as an additional security measure it is recommended to check permissions to the /etc/zabbix/zabbix_java_gateway_logback.xml file and set it read-only, if write permissions are available for the "zabbix" user.
If using a Zabbix version before 5.4.9, it is recommended to make sure that the "zabbix" user permissions to the /etc/zabbix/zabbix_java_gateway_logback.xml file are set to read-only only and the user cannot restart the Zabbix Java gateway service.

