安全设置 Zabbix 的最佳实践
概述
本章节包含为了以安全的方式设置 Zabbix 应遵守的最佳实践。
Zabbix 的功能不依赖于此处的实践。但建议使用它们以提高系统的安全性。
Access control
Principle of least privilege
The principle of least privilege should be used at all times for Zabbix. This principle means that user accounts (in Zabbix frontend) or process user (for Zabbix server/proxy or agent) have only those privileges that are essential to perform intended functions. In other words, user accounts at all times should run with as few privileges as possible.
Giving extra permissions to 'zabbix' user will allow it to access configuration files and execute operations that can compromise the overall security of the infrastructure.
When implementing the least privilege principle for user accounts, Zabbix frontend user types should be taken into account. It is important to understand that while a "Admin" user type has less privileges than "Super Admin" user type, it has administrative permissions that allow managing configuration and execute custom scripts.
Some information is available even for non-privileged users. For example, while Administration → Scripts is not available for non-Super Admins, scripts themselves are available for retrieval by using Zabbix API. Limiting script permissions and not adding sensitive information (like access credentials, etc) should be used to avoid exposure of sensitive information available in global scripts.
Zabbix agent 的安全用户
在默认的配置中,Zabbix server 和 Zabbix agent 进程共享一个“zabbix”用户。 如果您希望确保 Zabbix agent 无法访问 Zabbix server 配置中的敏感详细信息(例如,数据库登录信息),则应以不同的用户身份运行 Zabbix agent:
- 创建一个安全用户;
- 在 Zabbix agent 的 配置文件 中指定此用户(修改 'User' parameter);
- 以拥有管理员权限的用户重启 Zabbix agent。之后,此权限将赋予给先前指定的用户。
utf-8编码
UTF-8是Zabbix支持的唯一编码。 它可以正常工作而没有任何安全漏洞。 用户应注意,如果使用其他一些编码,则存在已知的安全问题
Windows installer paths
When using Windows installers, it is recommended to use default paths provided by the installer as using custom paths without proper permissions could compromise the security of the installation.
Zabbix Security Advisories and CVE database
See Zabbix Security Advisories and CVE database.
为 Zabbix 前端设置 SSL
在 RHEL/Centos 操作系统上,安装 mod_ssl 包:
为 SSL keys 创建目录:
创建 SSL 证书:
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/httpd/ssl/private/apache-selfsigned.key -out /etc/httpd/ssl/apache-selfsigned.crt下面提示内容适当填写。 最重要的一行是请求 Common Name 的行。 您需要输入要与服务器关联的域名。 如果您没有域名,则可以输入公共IP地址。 下面将使用 example.com。
Country Name (两个字母) [XX]:
State or Province Name (全名) []:
Locality Name (eg, city) [默认的城市]:
Organization Name (eg, company) [默认的公司名]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:example.com
Email Address []:编辑 Apache SSL 配置:
/etc/httpd/conf.d/ssl.conf
DocumentRoot "/usr/share/zabbix"
ServerName example.com:443
SSLCertificateFile /etc/httpd/ssl/apache-selfsigned.crt
SSLCertificateKeyFile /etc/httpd/ssl/private/apache-selfsigned.key重启 Apache 服务使以上修改的配置生效:
Web server hardening
在 URL 的根目录上启用 Zabbix
将虚拟主机添加到 Apache 配置,并将文档根目录的永久重定向设置为 Zabbix SSL URL。 不要忘记将 example.com 替换为服务器的实际名称。
/etc/httpd/conf/httpd.conf
#Add lines
<VirtualHost *:*>
ServerName example.com
Redirect permanent / http://example.com
</VirtualHost>重启 Apache 服务使以上修改的配置生效:
在Web服务器上启用HTTP严格传输安全性(HSTS)
为了保护Zabbix前端不受协议降级攻击,我们建议在Web服务器上启用HSTS策略
例如,要在Apache配置中为您的Zabbix前端启用HSTS策略:
将以下指令添加到虚拟主机的配置中:
重新启动Apache服务以应用更改:
在Web服务器上启用内容安全策略(CSP)
为了保护Zabbix前端免受跨站点脚本(XSS),数据注入和其他类似类型的攻击的影响,我们建议在Web服务器上启用内容安全策略。 为此,您需要配置Web服务器以返回Content-Security-Policy HTTP标头
要在Apache配置中为您的Zabbix前端启用CSP,请编辑:
例如,如果计划所有内容都来自站点的来源(不包括子域),则可以将以下指令添加到虚拟主机的配置中:
重新启动Apache服务以应用更改:
禁用曝光的 Web 服务器信息
建议在 Web 服务器强化过程中禁用所有 Web 服务器签名。 默认情况下,Web 服务器正在公开软件签名:
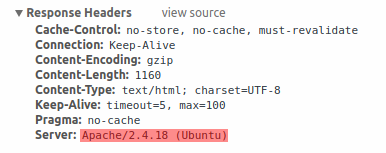
可以通过向 Apache(用作示例)配置文件添加两行来禁用签名:
可以通过更改 php.ini 配置文件来禁用 PHP 签名(X-Powered-By HTTP header)(默认情况下禁用签名):
若要应用配置文件更改,需要重新启动 Web 服务器。
通过在 Apache中 使用 mod_security( libapache2-mod-security2)可以实现额外的安全级别。 mod_security 允许删除服务器签名,而不是仅仅从服务器签名中删除版本。 通过在安装 mod_security 之后将“SecServerSignature”更改为任何所需的值,可以将签名更改为任何值。
请参阅 Web 服务器的文档以获取有关如何删除/更改软件签名的帮助。
禁用默认Web服务器错误页面
建议禁用默认错误页面以避免信息泄露。 Web服务器默认使用内置错误页面:
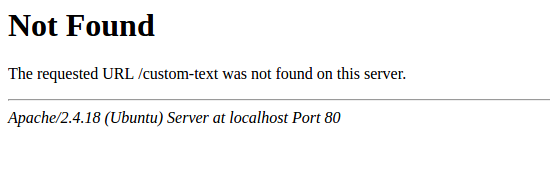
在Web服务器强化过程中,应替换/删除默认错误页面。 “ ErrorDocument”指令可用于为Apache Web服务器定义自定义错误页面/文本(用作示例)
请参考Web服务器的文档以找到有关如何替换/删除默认错误页面的帮助
Set X-Frame-Options HTTP response header
By default, Zabbix is configured with X-Frame-Options HTTP response header set to SAMEORIGIN, meaning that content can only be loaded in a frame that has the same origin as the page itself.
Zabbix frontend elements that pull content from external URLs (namely, the URL dashboard widget) display retrieved content in a sandbox with all sandboxing restrictions enabled.
These settings enhance the security of the Zabbix frontend and provide protection against XSS and clickjacking attacks. Super Admins can modify iframe sandboxing and X-Frame-Options HTTP response header parameters as needed. Please carefully weigh the risks and benefits before changing default settings. Turning sandboxing or X-Frame-Options off completely is not recommended.
Hiding the file with list of common passwords
To increase the complexity of password brute force attacks, it is suggested to limit access to the file ui/data/top_passwords.txt by modifying web server configuration. This file contains a list of the most common and context-specific passwords, and is used to prevent users from setting such passwords if Avoid easy-to-guess passwords parameter is enabled in the password policy.
For example, on NGINX file access can be limited by using the location directive:
On Apache - by using .htacess file:
Displaying URL content in the sandbox
Since version 5.0.2, some Zabbix frontend elements (for example, the URL dashboard widget) are preconfigured to sandbox content retrieved from the URL. It is recommended to keep all sandboxing restrictions enabled to ensure protection against XSS attacks.
在sandbox中显示URL内容
从5.0.2版开始,一些Zabbix前端元素(例如URL小部件)已预先配置为从URL检索的sandbox内容。 建议保持所有sandbox限制处于启用状态,以确保免受XSS攻击。
带有OPENSSL的在Windows上的zabbix agent
使用OpenSSL编译的Zabbix agent将尝试在c:\ openssl-64bit中访问SSL配置文件。 磁盘C:上的“ openssl-64bit”目录可以由非特权用户创建
因此,为了加强安全性,需要手动创建此目录并撤消非管理员用户的写访问权限
请注意,在Windows的32位和64位版本上,目录名称将有所不同

