5 Secure connection to the database
Overview
This section provides Zabbix setup steps and configuration examples for secure TLS connections between:
| Database | Zabbix components |
|---|---|
| MySQL | Zabbix frontend, Zabbix server, Zabbix proxy |
| PostgreSQL | Zabbix frontend, Zabbix server, Zabbix proxy |
To set up connection encryption within the DBMS, see official vendor documentation for details:
- MySQL: source and replica replication database servers.
- MySQL: group replication, etc. database servers.
- PostgreSQL encryption options.
All examples are based on the GA releases of MySQL CE (8.0) and PgSQL (13) available through official repositories using CentOS 8.
Requirements
The following is required to set up encryption:
- Developer-supported operating system with OpenSSL >=1.1.X or alternative.
It is recommended to avoid OS in the end-of-life status, especially in the case of new installations
- Database engine (RDBMS) installed and maintained from the official repository provided by developer. Operating systems often shipped with outdated database software versions for which encryption support is not implemented, for example RHEL 7 based systems and PostgreSQL 9.2, MariaDB 5.5 without encryption support.
Terminology
Setting this option enforces to use TLS connection to database from Zabbix server/proxy and frontend to database:
required- connect using TLS as transport mode without identity checksverify_ca- connect using TLS and verify certificateverify_full- connect using TLS, verify certificate and verify that database identity (CN) specified by DBHost matches its certificate
Zabbix configuration
Frontend to the database
A secure connection to the database can be configured during frontend installation:
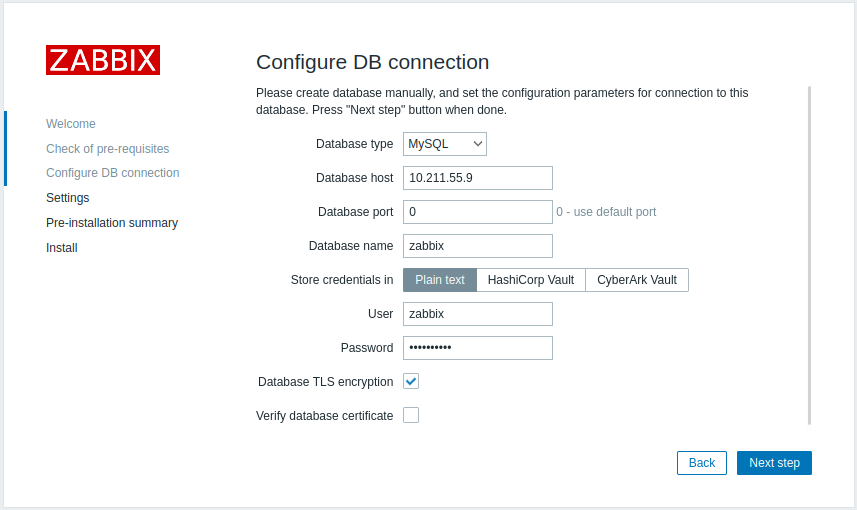
- Mark the Database TLS encryption checkbox in the Configure DB connection step to enable transport encryption.
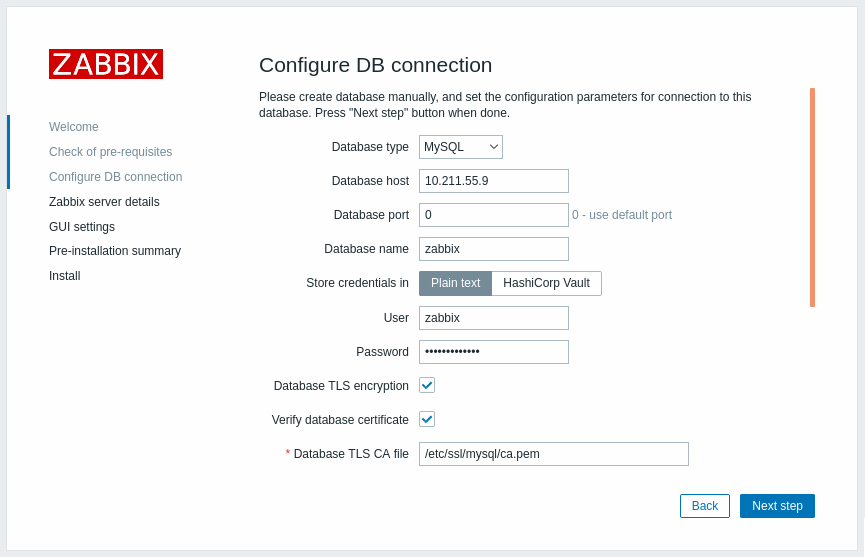
- Mark the Verify database certificate checkbox that appears when TLS encryption field is checked to enable encryption with certificates.
For MySQL, the Database TLS encryption checkbox is disabled, if Database host is set to localhost, because connection that uses a socket file (on Unix) or shared memory (on Windows) cannot be encrypted.
For PostgreSQL, the TLS encryption checkbox is disabled, if the value of the Database host field begins with a slash or the field is empty.
The following parameters become available in the TLS encryption in certificates mode (if both checkboxes are marked):
| Parameter | Description |
|---|---|
| Database TLS CA file | Specify the full path to a valid TLS certificate authority (CA) file. |
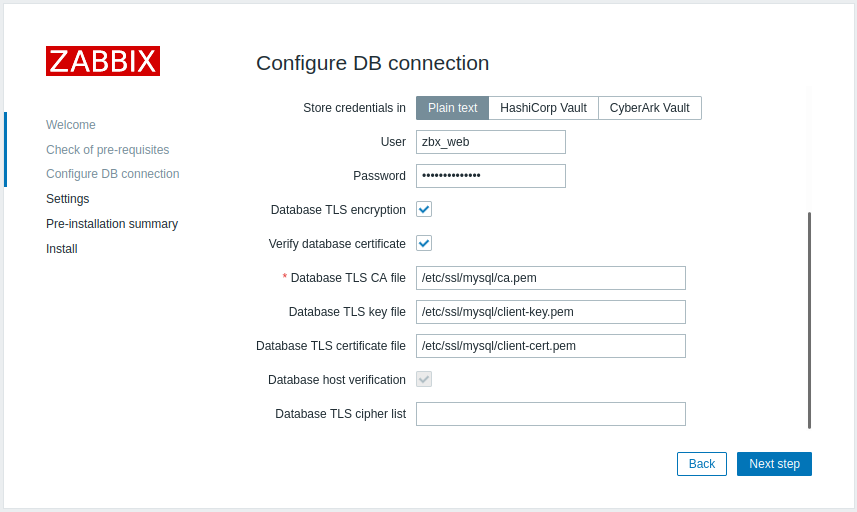
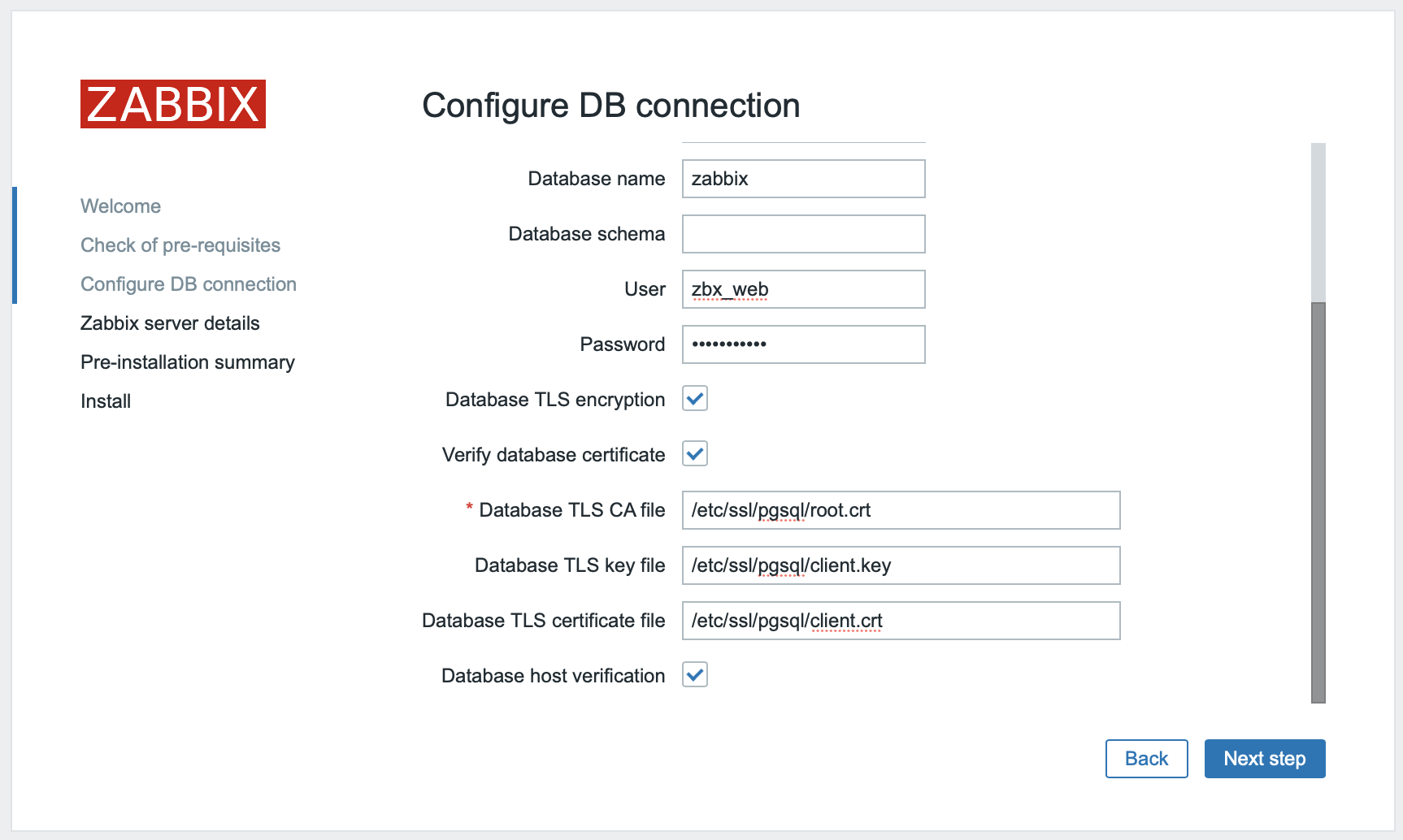
| Database TLS key file | Specify the full path to a valid TLS key file. |
| Database TLS certificate file | Specify the full path to a valid TLS certificate file. |
| Database host verification | Mark this checkbox to activate host verification. Disabled for MYSQL, because PHP MySQL library does not allow to skip the peer certificate validation step. |
| Database TLS cipher list | Specify a custom list of valid ciphers. The format of the cipher list must conform to the OpenSSL standard. Available for MySQL only. |
TLS parameters must point to valid files. If they point to non-existent or invalid files, it will lead to the authorization error.
If certificate files are writable, the frontend generates a warning in the System information report that "TLS certificate files must be read-only." (displayed only if the PHP user is the owner of the certificate).
Certificates protected by passwords are not supported.
Use cases
Zabbix frontend uses GUI interface to define possible options: required, verify_ca, verify_full. Specify required options in the installation wizard step Configure DB connections. These options are mapped to the configuration file (zabbix.conf.php) in the following manner:
| GUI settings | Configuration file | Description | Result |
|---|---|---|---|
 |
... // Used for TLS connection. $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = ''; $DB['CERT_FILE'] = ''; $DB['CA_FILE'] = ''; $DB['VERIFY_HOST'] = false; $DB['CIPHER_LIST'] = ''; ... |
Check Database TLS encryption Leave Verify database certificate unchecked |
Enable required mode. |
 |
... $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = ''; $DB['CERT_FILE'] = ''; $DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem'; $DB['VERIFY_HOST'] = false; $DB['CIPHER_LIST'] = ''; ... |
1. Check Database TLS encryption and Verify database certificate 2. Specify path to Database TLS CA file |
Enable verify_ca mode. |
 |
... // Used for TLS connection with strictly defined Cipher list. $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = '<key_file_path>'; $DB['CERT_FILE'] = '<key_file_path>'; $DB['CA_FILE'] = '<key_file_path>'; $DB['VERIFY_HOST'] = true; $DB['CIPHER_LIST'] = '<cipher_list>'; ... Or: ... // Used for TLS connection without Cipher list defined - selected by MySQL server $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = '<key_file_path>'; $DB['CERT_FILE'] = '<key_file_path>'; $DB['CA_FILE'] = '<key_file_path>'; $DB['VERIFY_HOST'] = true; $DB['CIPHER_LIST'] = ''; ... |
1. Check Database TLS encryption and Verify database certificate 2. Specify path to Database TLS key file 3. Specify path to Database TLS CA file 4. Specify path to Database TLS certificate file 5. Specify Database TLS cipher list (optional) |
Enable verify_full mode for MySQL. |
 |
... $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = '<key_file_path>'; $DB['CERT_FILE'] = '<key_file_path>'; $DB['CA_FILE'] = '<key_file_path>'; $DB['VERIFY_HOST'] = true; $DB['CIPHER_LIST'] = ' '; ... |
1. Check Database TLS encryption and Verify database certificate 2. Specify path to Database TLS key file 3. Specify path to Database TLS CA file 4. Specify path to Database TLS certificate file 5. Check Database host verification |
Enable verify_full mode for PostgreSQL. |
See also: Encryption configuration examples for MySQL, Encryption configuration examples for PostgreSQL.
Zabbix server/proxy configuration
Secure connections to the database can be configured with the respective parameters in the Zabbix server and/or proxy configuration file.
| Configuration | Result |
|---|---|
| None | Connection to the database without encryption. |
1. Set DBTLSConnect=required |
Server/proxy make a TLS connection to the database. An unencrypted connection is not allowed. |
1. Set DBTLSConnect=verify_ca2. Set DBTLSCAFile - specify the TLS certificate authority file |
Server/proxy make a TLS connection to the database after verifying the database certificate. |
1. Set DBTLSConnect=verify_full2. Set DBTLSCAFile - specify TLS certificate authority file |
Server/proxy make a TLS connection to the database after verifying the database certificate and the database host identity. |
1. Set DBTLSCAFile - specify TLS certificate authority file2. Set DBTLSCertFile - specify the client public key certificate file3. Set DBTLSKeyFile - specify the client private key file |
Server/proxy provide a client certificate while connecting to the database. |
1. Set DBTLSCipher - the list of encryption ciphers that the client permits for connections using TLS protocols up to TLS 1.2or DBTLSCipher13 - the list of encryption ciphers that the client permits for connections using TLS 1.3 protocol |
(MySQL) TLS connection is made using a cipher from the provided list. (PostgreSQL) Setting this option will be considered as an error. |

