12 使用 Okta 设置 SAML
本节提供配置 Okta 以启用 Zabbix 的 SAML 2.0 身份验证和用户配置的指南。
Okta 配置
1. 前往 https://developer.okta.com/signup/ 并注册/登录您的帐户。
2. 在 Okta Web 界面中导航至 应用程序 → 应用程序。
3. 单击 创建应用程序集成。
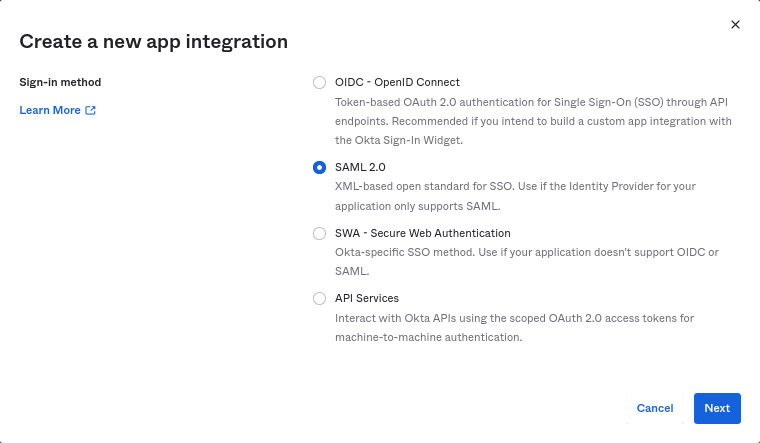
选择“SAML 2.0”作为登录方法,然后单击 下一步。
4. 在常规设置中,填写应用程序名称,然后单击 下一步。
5. 在 SAML 配置中,输入下面提供的值,然后
单击 下一步。
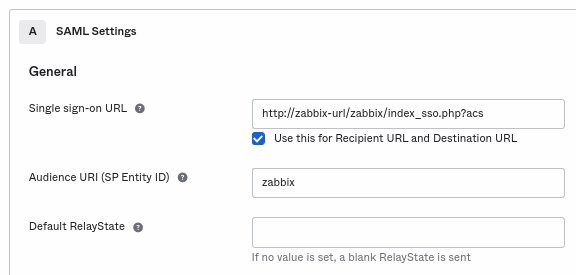
- 在 General 中添加:
- 单点登录 URL:
http://<your-zabbix-url>/zabbix/index_sso.php?acs
请注意使用“http”,而不是“https”,这样acs参数就不会在请求中被截断。还应标记 将其用于收件人 URL 和目标 URL 复选框。 - 受众 URI(SP 实体 ID):
zabbix
请注意,此值将在 SAML 断言中用作 唯一服务提供商标识符(如果不匹配,则 操作将被拒绝)。可以在此字段中指定 URL 或 任何数据字符串。 - 默认 RelayState:
将此字段留空;如果需要自定义重定向,可以在 Zabbix 的 用户 → 用户 设置中添加。 - 根据您的偏好填写其他字段。
- 在 属性语句/组属性语句 中添加:
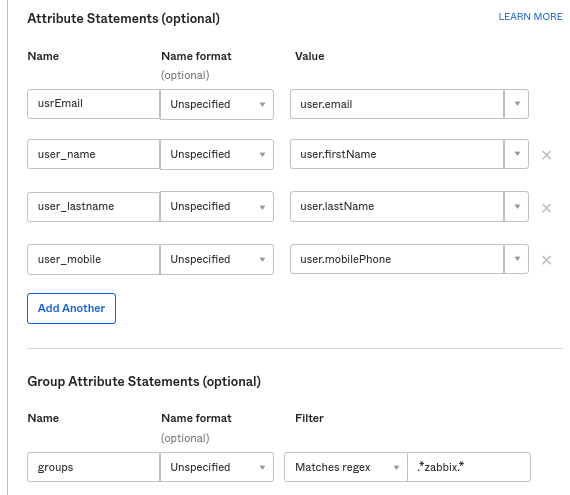 这些属性语句插入到与 Zabbix 共享的 SAML 断言中。 此处使用的属性名称是任意示例。您可以使用不同的属性名称,但是,它们必须与 Zabbix SAML 设置中的相应字段值匹配。 如果您想在没有 JIT 用户配置的情况下将 SAML 登录配置到 Zabbix,则只需要电子邮件属性。 :: noteclassic 如果计划使用加密连接,请生成私有和公共加密证书,然后将公共证书上传到 Okta。当“断言加密”设置为“已加密”时,将出现证书上传表单(单击“显示高级设置”以找到此参数)。 :::
这些属性语句插入到与 Zabbix 共享的 SAML 断言中。 此处使用的属性名称是任意示例。您可以使用不同的属性名称,但是,它们必须与 Zabbix SAML 设置中的相应字段值匹配。 如果您想在没有 JIT 用户配置的情况下将 SAML 登录配置到 Zabbix,则只需要电子邮件属性。 :: noteclassic 如果计划使用加密连接,请生成私有和公共加密证书,然后将公共证书上传到 Okta。当“断言加密”设置为“已加密”时,将出现证书上传表单(单击“显示高级设置”以找到此参数)。 :::
6. 在下一个选项卡中,选择“我是软件供应商。我想将我的应用程序与 Okta 集成”,然后按“完成”。
7. 导航到新创建的应用程序的“分配”选项卡,然后单击“分配”按钮,然后从下拉菜单中选择“分配给人员”。
8. 在出现的弹出窗口中,将应用程序分配给将使用 SAML 2.0 与 Zabbix 进行身份验证的人员,然后单击“保存并返回”。
9. 导航到“登录”选项卡,然后单击“查看设置说明”按钮。
安装说明将在新选项卡中打开;配置 Zabbix 时保持此选项卡打开。
Zabbix 配置
1. 在 Zabbix 中,转到 SAML 设置 并根据 Okta 的设置说明填写配置选项:
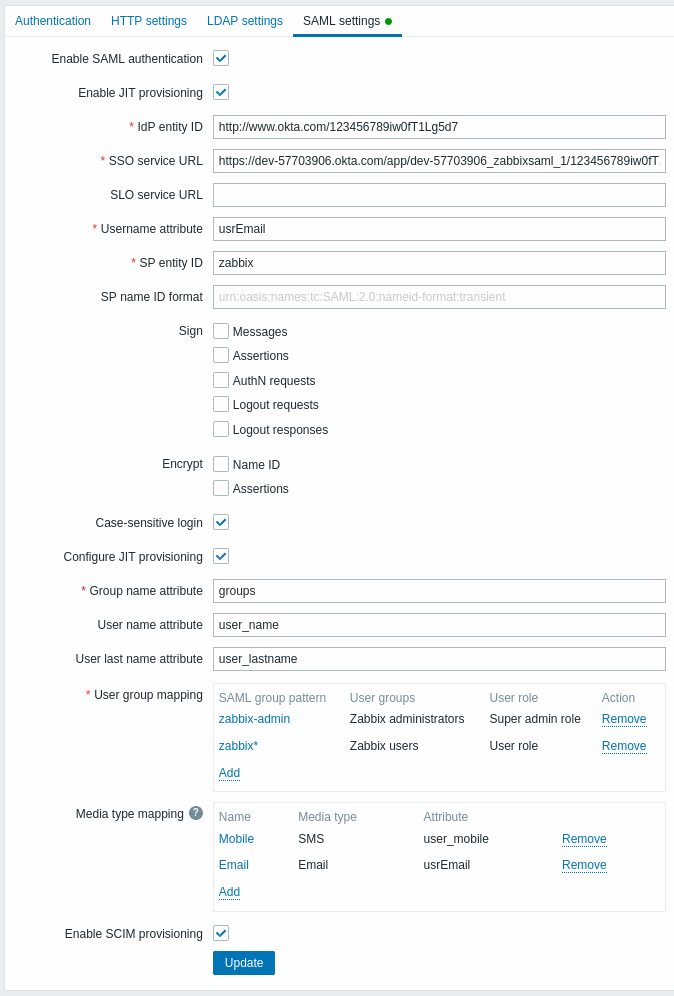
| Zabbix 字段 | Okta 中的设置字段 | 示例值 |
|---|---|---|
| IdP 实体 ID | 身份提供商发行者 | |
| SSO 服务 URL | 身份提供商单点登录 URL | |
| 用户名属性 | 属性名称 | usrEmail |
| SP 实体 ID | 受众 URI | zabbix |
| 组名称属性 | 属性名称 | groups |
| 用户名属性 | 属性名称 | user_name |
| 用户姓氏属性 | 属性名称 | user_lastname |
还需要配置用户组和媒体映射。
2. 将 Okta SAML 设置说明中提供的证书 下载到 ui/conf/certs 文件夹中,作为 idp.crt。
通过运行以下命令为其设置 644 权限:
chmod 644 idp.crt
3. 如果 Okta 中的 断言加密 已设置为“加密”,则 Zabbix 中也应勾选 加密 参数的 “断言”复选框。
4. 按“更新”按钮保存这些设置。
SCIM 配置
1. 要打开 SCIM 配置,请转到 Okta 中应用程序的“常规”->“应用程序设置”。
选中 启用 SCIM 配置 复选框。结果,会出现一个新的 配置 选项卡。
2.转到“Provisioning”选项卡以设置 SCIM 连接:
- 在 SCIM 连接器基本 URL 中指定 Zabbix 前端的路径并将
api_scim.php附加到其中,即:
https://<your-zabbix-url>/zabbix/api_scim.php - 用户的唯一标识符字段:
email - 身份验证模式:
HTTP header - 在 授权 中输入具有超级管理员权限的有效 API 令牌
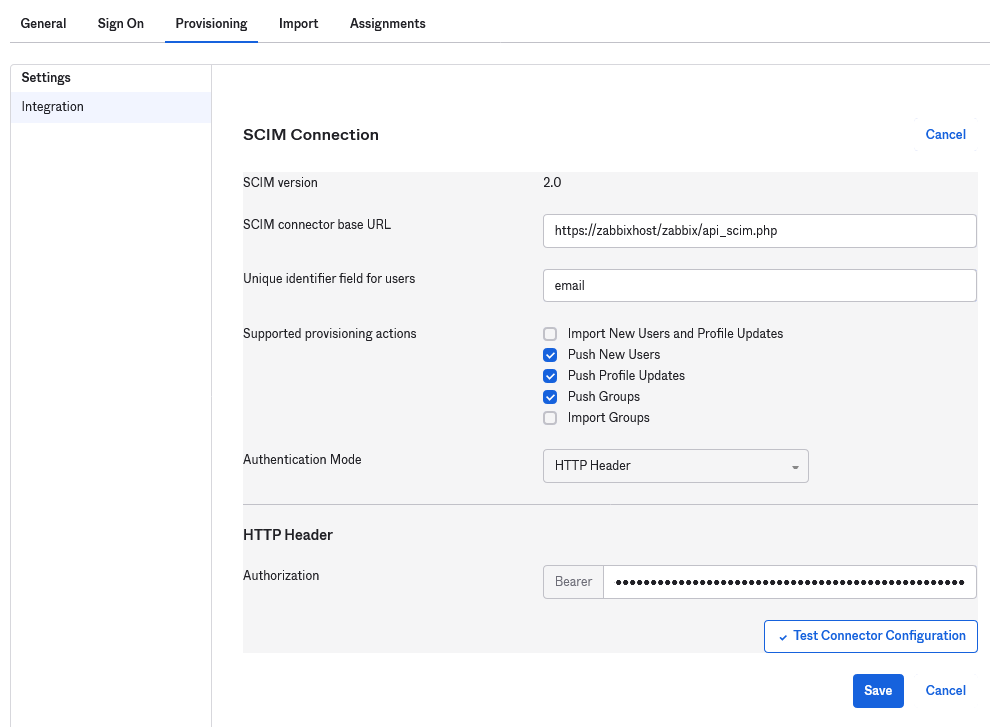
如果您使用的是 Apache,则可能需要通过添加以下行来更改 /etc/apache2/apache2.conf 中的默认 Apache 配置:
SetEnvIf Authorization "(.*)" HTTP_AUTHORIZATION=$1
否则Apache 不会在请求中发送授权标头。
3. 单击 测试连接器配置 以测试连接。如果一切正确,将显示成功消息。
4. 在“配置”->“到应用程序”中,确保选中以下复选框:
- 创建用户
- 更新用户属性
- 停用用户
这将确保这些请求类型将发送到 Zabbix。
5. 确保 SAML 中定义的所有属性都在 SCIM 中定义。您可以通过单击 转到配置文件编辑器 在“配置”->“到应用程序”中访问应用程序的配置文件编辑器。
单击 添加属性。使用 SAML 属性名称填充 显示名称、变量名称、外部名称 的值,例如 user_name。
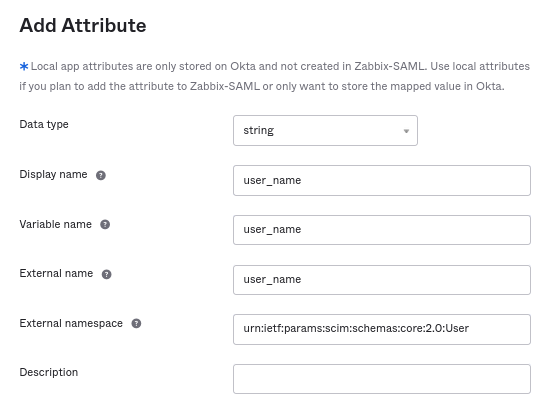
外部命名空间应与用户架构相同:urn:ietf:params:scim:schemas:core:2.0:User
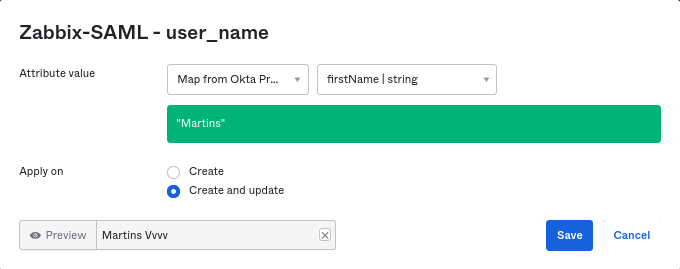
6. 转到应用程序的“配置”->“到应用程序”->“属性映射”。单击底部的显示未映射的属性。新添加的属性出现。
7. 映射每个添加的属性。
8. 在“分配”选项卡中添加用户。之前需要在目录->人员中添加用户。所有这些分配都将作为请求发送到 Zabbix。
9.在“推送组”选项卡中添加组。Zabbix SAML 设置中的用户组映射模式必须与此处指定的组匹配。如果不匹配,则无法在 Zabbix 中创建用户。
每次发生更改时都会发送有关组成员的信息。

