Join our translation project and help translate Zabbix documentation into your native language.
5 What's new in Zabbix 8.0.0
Zabbix 8.0.0 continues from Zabbix 7.4.0, adding new features and enhancements.
See breaking changes for this version.
Templates
New templates
- Aruba CX 8300s by SNMP, a template providing SNMP-based monitoring for the Aruba CX 8300 switch series.
- The AWS by HTTP template set has been supplemented with the template AWS Backup Vault by HTTP.
- Ciena 3906 by SNMP, a template for monitoring Ciena 3906 devices.
- Cisco Secure Firewall Threat Defense by HTTP, a template providing monitoring capabilities for Cisco Secure Firewall Threat Defense devices using REST API.
- OpenAI Platform by HTTP, a template for monitoring OpenAI's developer platform.
- Stormshield SNS by SNMP, a template for monitoring Stormshield Network Security (SNS) devices via SNMP.
- Vyatta Virtual Router by SNMP, a template for monitoring the Vyatta 1908e virtual router.
Updated templates
- The Proxmox VE by HTTP template has been updated with the nested LLD functionality. In addition, the unit format for items displaying percentages has been adjusted for clarity.
- MySQL by Zabbix agent, MySQL by Zabbix agent 2, MySQL by Zabbix agent active, MySQL by Zabbix agent 2 active, and MySQL by ODBC have been updated to support both
SHOW SLAVE STATUS(old syntax) andSHOW REPLICA STATUS(new syntax).
Frontend
Inline validation in autoregistration form
The autoregistration action configuration form in the frontend now supports inline validation. Input errors are displayed immediately after filling in the fields, improving usability and reducing configuration mistakes.
Importable SAML certificates for single sign-on
Super admin users can now import certificates and private keys directly in the frontend for SAML configuration. Three new fields were added to Administration > Authentication > SAML:
- IdP certificate - X.509 certificate presented by the identity provider
- SP certificate - service provider certificate used for SAML exchanges
- SP private key - private key corresponding to the SP certificate
These controls allow adding new values or modifying existing ones from the SAML settings tab. Certificates and private keys are validated before being saved to the chosen storage backend; invalid or malformed values are rejected with an explanatory error.
Convert to JSON checkbox in discovery forms
A new Convert to JSON checkbox was added to the Discovery rule form and Discovery prototype form, which is shown if "HTTP agent" is selected in the Type dropdown. This option allows to mark retrieved data for automatic conversion to JSON before further processing.
New and embedded fonts
Zabbix now includes new and embedded fonts that improve readability, load faster, and render additional frontend languages with minimal layout impact. Being embedded, these fonts also ensure a consistent appearance across systems.
New fonts: |
Legacy fonts: |
The new fonts are used in almost all themes. If needed, the newly added Blue (classic) and Dark (classic) themes are available with legacy fonts.
The font family for monospace content and graphs remains unchanged.
Modal forms
In low-level discovery setup, the host prototype configuration form is now opened in a modal (pop-up) window.
Widgets
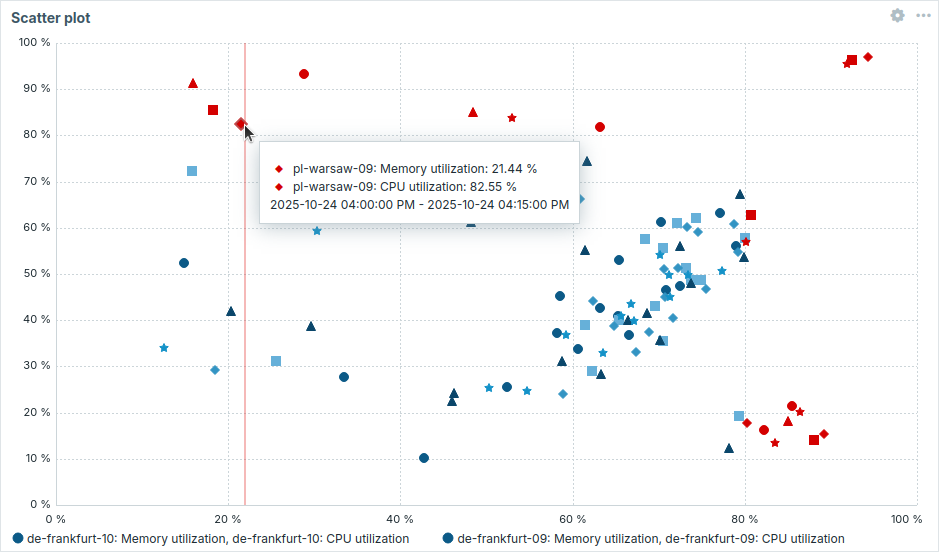
Scatter plot
The Scatter plot widget has been added to dashboard widgets. It displays the relationship between two metrics by plotting individual data points along an X and Y axis. This helps reveal patterns, clusters, correlations, and outliers in the data set.
Geomap host marker clustering
The Geomap widget now supports a Clustering parameter to control how nearby host markers are combined into a single marker with a count. By setting the map zoom level for clustering, you can keep large maps readable and maintain precise visibility when zoomed in.
Documentation
Consolidated documentation pages for minor releases
Release documentation for minor versions of a major Zabbix release will now be collected in single documentation pages for new features and upgrade notes respectively.
Processes
SNMPv3 EngineID caching and reuse
Zabbix now caches SNMPv3 EngineID → IP mappings and will attempt to reuse cached EngineIDs for subsequent SNMPv3 checks, reducing probe traffic and improving poller performance. If a reused EngineID does not respond, the poller falls back to an EngineID probe and may remove stale entries after interface changes or persistent failures.
Refined proxy throttling during history cache recovery
Proxy throttling logic has been refined to improve server stability during history cache recovery. When history cache usage reaches the throttling threshold, the server continues to stop accepting proxy data as before. When cache usage falls to 60%, the server begins processing the throttling list but may still reject proxy uploads that contain very large batches (approximately more than 10k records) until cache pressure decreases further. This change reduces the risk of repeated cache overloads while the server recovers.
Increased maximum timeout for the zabbix_get and zabbix_js
The maximum value for the timeout parameter of the zabbix_get and zabbix_js command-line utilities has been increased to 600 seconds.
Event cleanup by housekeeper for deleted triggers
When a trigger is deleted, the housekeeper now also removes all events associated with problems from that trigger. Previously, only the trigger's problems were removed, while events were removed only after the housekeeper Trigger data storage period expired.
Manual close — trigger tags inherited by recovery events
Recovery events created after a manual close inherit trigger tags in addition to item and host tags. These tags are present in the event tags array and are available to notification macros such as {EVENT.RECOVERY.TAGS} and {EVENT.RECOVERY.TAGSJSON}.
Items
smart.disk.discovery — new type parameter
The smart.disk.discovery item (Zabbix agent 2 S.M.A.R.T. plugin) now accepts an optional type parameter to specify a value to scan for the disks.
Plugins
Ceph plugin
This plugin now operates in two modes:
- native - This mode uses the go-ceph library to communicate directly with the Ceph cluster using the native Ceph API (msgr2 protocol). This is the recommended mode for modern Ceph installations, but is only supported on Linux and starting with Ceph 16.
- restful (deprecated) - This mode uses the Ceph RESTful API for communication. It is the default mode for backward compatibility but will not work with Ceph version 20 (Tentacle) or newer due to the removal of the mgr/restful module.
Which mode to use is determined by the value of the mode parameter (native/restful):
Plugins.Ceph.Default.Mode=native- set the native mode for the pluginPlugins.Ceph.Sessions.<SessionName>.Mode=native- set the native mode for the named session
Note that the user credential set differs for each mode and they are not compatible with each other. The Plugins.Ceph.InsecureSkipVerify parameter is ignored in native mode because connection security is defined on the Ceph cluster side by msgr2 protocol (secure by default).
Note that the Ceph plugin for Zabbix agent 2 is now a loadable plugin and requires additional installation steps. This is due to the librados package requirement (for the native mode). See the Ceph plugin readme for details.
Test execution mode for loadable plugins
Loadable plugins can now be launched in test mode using the -t (--test) flag, passing an item key as argument. In this mode, the plugin runs for debugging and development purposes, and plugin configuration files are ignored.
Redis plugin — TLS support and startup-time validation
TLS support has been added to the Redis plugin for Zabbix agent 2.
Startup-time validation of the plugin TLS configuration was implemented and validation/error messages improved. An invalid configuration logic (for example: using connection type verify_full without specifying TLSCAFile) can prevent Zabbix agent 2 from starting.
Low-level discovery
Macro support for nested low-level discovery
Low-level discovery macros are now supported in nested low-level discovery rules, in:
- JSONPath preprocessing parameters
- JSONPath field for custom LLD macros
