5 Ролі користувачів
Огляд
У розділі Адміністрування → Ролі користувачів зберігаються ролі, які можна призначати користувачам системи, і спеціальні дозволи для кожної ролі.
Default user roles
By default, Zabbix is configured with four user roles, which have a pre-defined set of permissions:
- Admin role
- Guest role
- Super admin role
- User role
Default Super admin role cannot be modified or deleted, because at least one Super admin user with unlimited privileges must exist in Zabbix.
Zabbix users with type Super admins and proper permissions can modify or delete existing roles or create new custom roles.
To create a new role, click on the Create user role button at the top right corner. To update an existing role, press on the role name to open the configuration form.
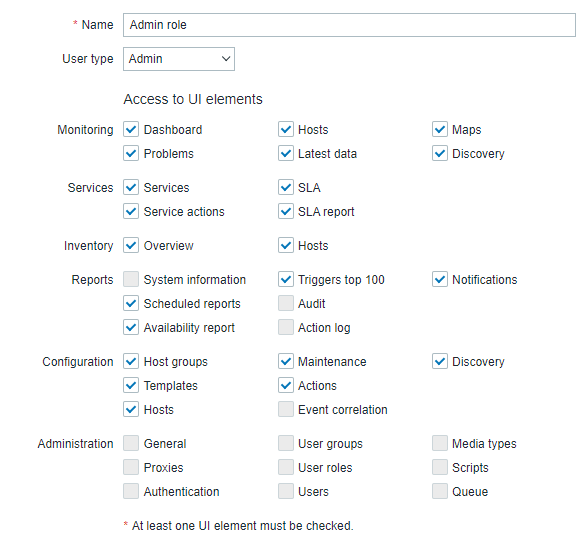
Available permission options along with default permission sets for pre-existing user roles in Zabbix are described below.
| Parameter | Description | Default user roles | |||
|---|---|---|---|---|---|
| Super admin role | Admin role | User role | Guest role | ||
| Name | Role visible name. | Super admin role | Admin role | User role | Guest role |
| User type | Selected user type determines the list of available permissions. Upon selecting a user type, all available permissions for this user type are granted by default. Uncheck the checkbox(es) to revoke certain permissions for the user role. Checkboxes for permissions not available for this user type are grayed out. |
Super admin | Admin | User | User |
| Access to UI elements | |||||
| Monitoring | |||||
| Dashboard | Enable/disable access to a specific Monitoring menu section and underlying pages. | Yes | Yes | Yes | Yes |
| Problems | |||||
| Hosts | |||||
| Latest data | |||||
| Maps | |||||
| Discovery | No | No | |||
| Services | Yes | Yes | |||
| Inventory | |||||
| Overview | Enable/disable access to a specific Inventory menu section and underlying pages. | Yes | Yes | Yes | Yes |
| Hosts | |||||
| Reports | |||||
| System information | Enable/disable access to a specific Reports menu section and underlying pages. | Yes | No | No | No |
| Availability report | Yes | Yes | Yes | ||
| Triggers top 100 | |||||
| Audit | No | No | No | ||
| Action log | |||||
| Notifications | Yes | ||||
| Scheduled reports | |||||
| Configuration | |||||
| Host groups | Enable/disable access to a specific Configuration menu section and underlying pages. | Yes | Yes | No | No |
| Templates | |||||
| Hosts | |||||
| Maintenance | |||||
| Actions | |||||
| Event correlation | No | ||||
| Discovery | Yes | ||||
| Administration | |||||
| General | Enable/disable access to a specific Administration menu section and underlying pages. | Yes | No | No | No |
| Proxies | |||||
| Authentication | |||||
| User groups | |||||
| User roles | |||||
| Users | |||||
| Media types | |||||
| Scripts | |||||
| Queue | |||||
| Default access to new UI elements | Enable/disable access to the custom UI elements. Modules, if present, will be listed below. | Yes | Yes | Yes | Yes |
| Access to services | |||||
| Read-write access to services | Select read-write access to services: None - no access at all All - access to all services is read-write Service list - select services for read-write access The read-write access takes precedence over the read-only access and is dynamically inherited by the child services. |
Yes | Yes | No | No |
| Read-write access to services with tag | Specify tag name and, optionally, value to additionally grant read-write access to services matching the tag. This option is available if 'Service list' is selected in the Read-write access to services parameter. The read-write access takes precedence over the read-only access and is dynamically inherited by the child services. |
||||
| Read-only access to services | Select read-only access to services: None - no access at all All - access to all services is read-only Service list - select services for read-only access The read-only access does not take precedence over the read-write access and is dynamically inherited by the child services. |
||||
| Read-only access to services with tag | Specify tag name and, optionally, value to additionally grant read-only access to services matching the tag. This option is available if 'Service list' is selected in the Read-only access to services parameter. The read-only access does not take precedence over the read-write access and is dynamically inherited by the child services. |
||||
| Access to modules | |||||
| <Module name> | Allow/deny access to a specific module. Only enabled modules are shown in this section. It is not possible to grant or restrict access to a module that is currently disabled. | Yes | Yes | Yes | Yes |
| Default access to new modules | Enable/disable access to modules that may be added in the future. | ||||
| Access to API | |||||
| Enabled | Enable/disable access to API. | Yes | Yes | Yes | No |
| API methods | Select Allow list to allow only specified API methods or Deny list to restrict only specified API methods. In the search field, start typing the method name, then select the method from the auto-complete list. You can also press the Select button and select methods from the full list available for this user type. Note, that if certain action from the Access to actions block is unchecked, users will not be able to use API methods related to this action. Wildcards are supported. Examples: dashboard.* (all methods of 'dashboard.' API service) * (any method), *.export (methods with '.export' name from all API services).If no methods have been specified the Allow/Deny list rule will be ignored. |
||||
| Access to actions | |||||
| Create and edit dashboards | Clearing this checkbox will also revoke the rights to use .create, .update and .delete API methods for the corresponding elements. |
Yes | Yes | Yes | No |
| Create and edit maps | |||||
| Create and edit maintenance | No | ||||
| Add problem comments | Clearing this checkbox will also revoke the rights to perform corresponding action via event.acknowledge API method. |
Yes | |||
| Change severity | |||||
| Acknowledge problems | |||||
| Close problems | |||||
| Execute scripts | Clearing this checkbox will also revoke the rights to use the script.execute API method. |
||||
| Manage API tokens | Clearing this checkbox will also revoke the rights to use all token. API methods. |
||||
| Manage scheduled reports | Clearing this checkbox will also revoke the rights to use all report. API methods. |
No | |||
| Default access to new actions | Enable/disable access to new actions. | Yes | |||
Notes:
- Each user may have only one role assigned.
- If an element is restricted, users will not be able to access it even by entering a direct URL to this element into the browser.
- Users of type User or Admin cannot change their own role settings.
- Users of type Super admin can modify settings of their own role (not available for the default Super admin role), but not the user type.
- Users of all levels cannot change their own user type.
See also:

