1 MySQL 加密配置
概述
本节提供针对CentOS 8.2和MySQL 8.0.21的若干加密配置示例,可作为快速入门指南用于加密数据库连接。
若 MySQL 主机设置为localhost,加密选项将不可用。此时Zabbix前端与数据库之间的连接会使用套接字file(Unix系统)或共享内存memory(Windows系统),且无法进行加密。
加密组合方案不仅限于本页所列内容,实际存在更多可用组合。
先决条件
从official repository安装MySQL数据库.
有关如何使用MySQL仓库的详细信息,请参阅MySQL documentation.
MySQL服务器已准备就绪,可使用自签名证书接受安全连接.
要查看哪些用户正在使用加密连接,请run以下query(需开启Performance Schema):
mysql> SELECT sbt.variable_value AS tls_version, t2.variable_value AS cipher, processlist_user AS user, processlist_host AS 主机 FROM performance_schema.status_by_thread AS sbt JOIN performance_schema.threads AS t ON t.thread_id = sbt.thread_id JOIN performance_schema.status_by_thread AS t2 ON t2.thread_id = t.thread_id WHERE sbt.variable_name = 'Ssl_version' and t2.variable_name = 'Ssl_cipher' ORDER BY tls_version;
仅传输加密
MySQL配置
现代版本的数据库已为required提供开箱即用的支持 术语. A 服务器端证书将在初始设置和启动后创建。
为主组件创建用户和角色:
mysql> CREATE USER
'zbx_srv'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>',
'zbx_web'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>'
REQUIRE SSL
PASSWORD HISTORY 5;
mysql> CREATE ROLE 'zbx_srv_role', 'zbx_web_role'; mysql> 创建角色 'zbx_srv_role', 'zbx_web_role';
mysql> GRANT SELECT, UPDATE, DELETE, INSERT, CREATE, DROP, ALTER, INDEX, REFERENCES ON zabbix.* TO 'zbx_srv_role';
mysql> GRANT SELECT, UPDATE, DELETE, INSERT ON zabbix.* TO 'zbx_web_role';
mysql> GRANT 'zbx_srv_role' TO 'zbx_srv'@'%';
mysql> GRANT 'zbx_web_role' TO 'zbx_web'@'%';
mysql> SET DEFAULT ROLE 'zbx_srv_role' TO 'zbx_srv'@'%';
mysql> SET DEFAULT ROLE 'zbx_web_role' TO 'zbx_web'@'%';请注意,X.509协议并非用于身份验证,而是用于 user is configured to use only encrypted connections. See MySQL documentation 有关配置用户的更多详情。
运行以检查连接(无法使用套接字连接测试安全连接) 连接):
检查当前状态及可用加密套件:
mysql> status
--------------
mysql Ver 8.0.21 for Linux on x86_64 (MySQL Community Server - GPL)
连接ID: 62
Current database:
Current user: [email protected]
SSL: Cipher in use is TLS_AES_256_GCM_SHA384
mysql> SHOW SESSION STATUS LIKE 'Ssl_cipher_list'\G;
*************************** 1. 行 ***************************
Variable_name: Ssl_cipher_list变量名称: Ssl_cipher_list 值: TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:TLS_AES_128_CCM_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-DSS-AES128-SHA256:DHE-DSS-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-DSS-AES128-SHA:DHE-RSA-AES128-SHA:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES256-SHA:CAMELLIA256-SHA:CAMELLIA128-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA 1 行记录已返回 (0.00 秒)
错误: 未指定query
前端
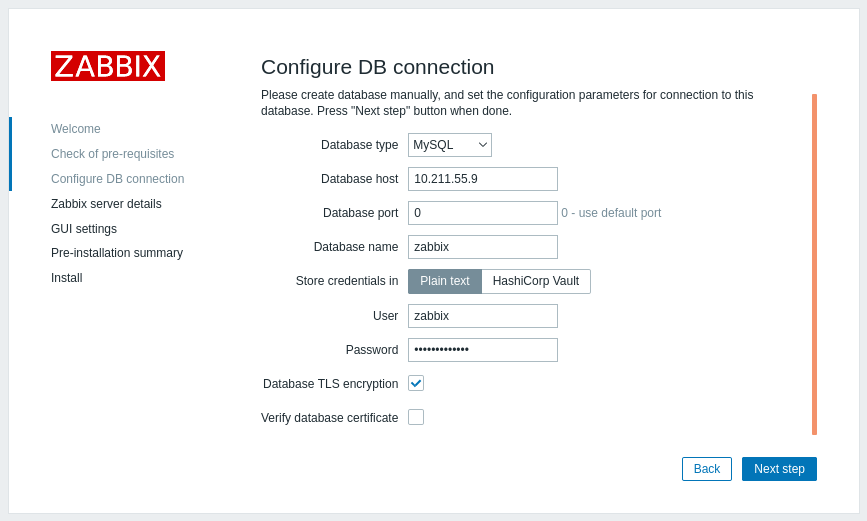
要为Zabbix前端与数据库之间的连接启用仅传输加密:
- 勾选数据库TLS加密
- 保持验证数据库证书未勾选状态
Server
要为服务器与数据库之间的连接启用仅传输加密,请配置 /etc/zabbix/zabbix_server.conf 文件:
... DBHost=10.211.55.9 DBName=zabbix DBUser=zbx_srv DBPassword=<strong_password> DBTLSConnect=required ...
带CA验证的加密
将所需的MySQL CA证书复制到Zabbix前端服务器,并分配适当权限以允许web服务器读取该file。
由于MySQL库版本较旧,此模式在SLES 12和RHEL 7上无法工作。
前端
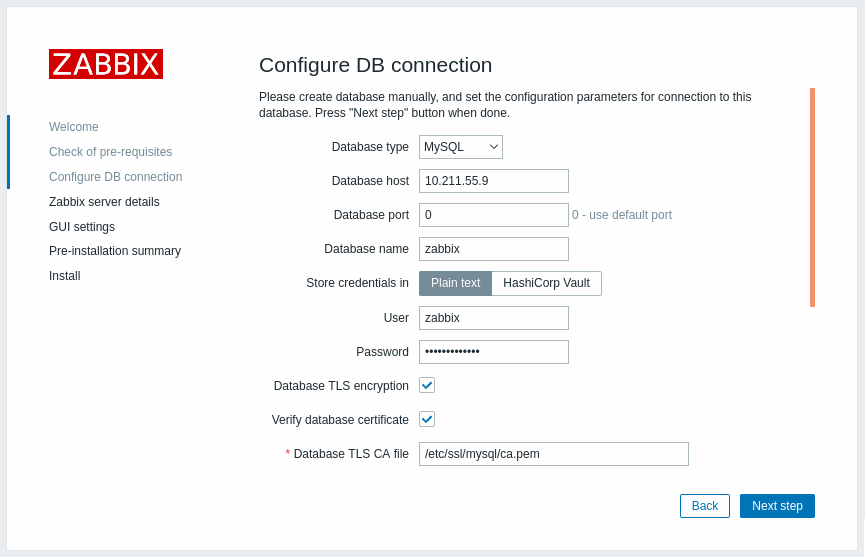
要为Zabbix前端与数据库之间的连接启用证书验证加密:
- 勾选数据库TLS加密和验证数据库证书
- 指定数据库TLS CA证书路径file
或者,可以在/etc/zabbix/web/zabbix.conf.php文件中设置:
...
$DB['ENCRYPTION'] = true;
$DB['KEY_FILE'] = '';
$DB['CERT_FILE'] = '';
$DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem';
$DB['VERIFY_HOST'] = false;
$DB['CIPHER_LIST'] = '';
...使用命令行工具排查用户连接问题,检查指定用户是否能建立连接:
mysql -u zbx_web -p -h 10.211.55.9 --ssl-mode=REQUIRED --ssl-ca=/var/lib/mysql/ca.pem
Server
要为Zabbix server与数据库之间的连接启用证书验证加密 请配置 /etc/zabbix/zabbix_server.conf 文件:
... DBHost=10.211.55.9 DBName=zabbix DBUser=zbx_srv DBPassword=<strong_password> DBTLSConnect=verify_ca DBTLSCAFile=/etc/ssl/mysql/ca.pem ...
完全验证加密
MySQL配置
设置MySQL CE服务器配置选项 (/etc/my.cnf.d/server-tls.cnf)为:
[mysqld]
...
# in this examples keys are located in the MySQL CE datadir directory
ssl_ca=ca.pem
ssl_cert=server-cert.pem
ssl_key=server-key.pem
require_secure_transport=ON
tls_version=TLSv1.3
...MySQL CE服务器和客户端(Zabbix前端)的密钥应 根据MySQL CE文档手动创建: Creating SSL and RSA certificates and keys using MySQL 或 Creating SSL certificates and keys using openssl
MySQL服务器证书应包含 Common Name字段设置为FQDN名称,因为Zabbix前端将使用 数据库的DNS名称或IP地址与数据库通信 主机.
创建MySQL用户:
mysql> CREATE USER
'zbx_srv'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>',
'zbx_web'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>'
REQUIRE X509
PASSWORD HISTORY 5;检查是否可以使用该用户登录:
mysql -u zbx_web -p -h 10.211.55.9 --ssl-mode=VERIFY_IDENTITY --ssl-ca=/var/lib/mysql/ca.pem --ssl-cert=/var/lib/mysql/client-cert.pem --ssl-key=/var/lib/mysql/client-key.pem
前端
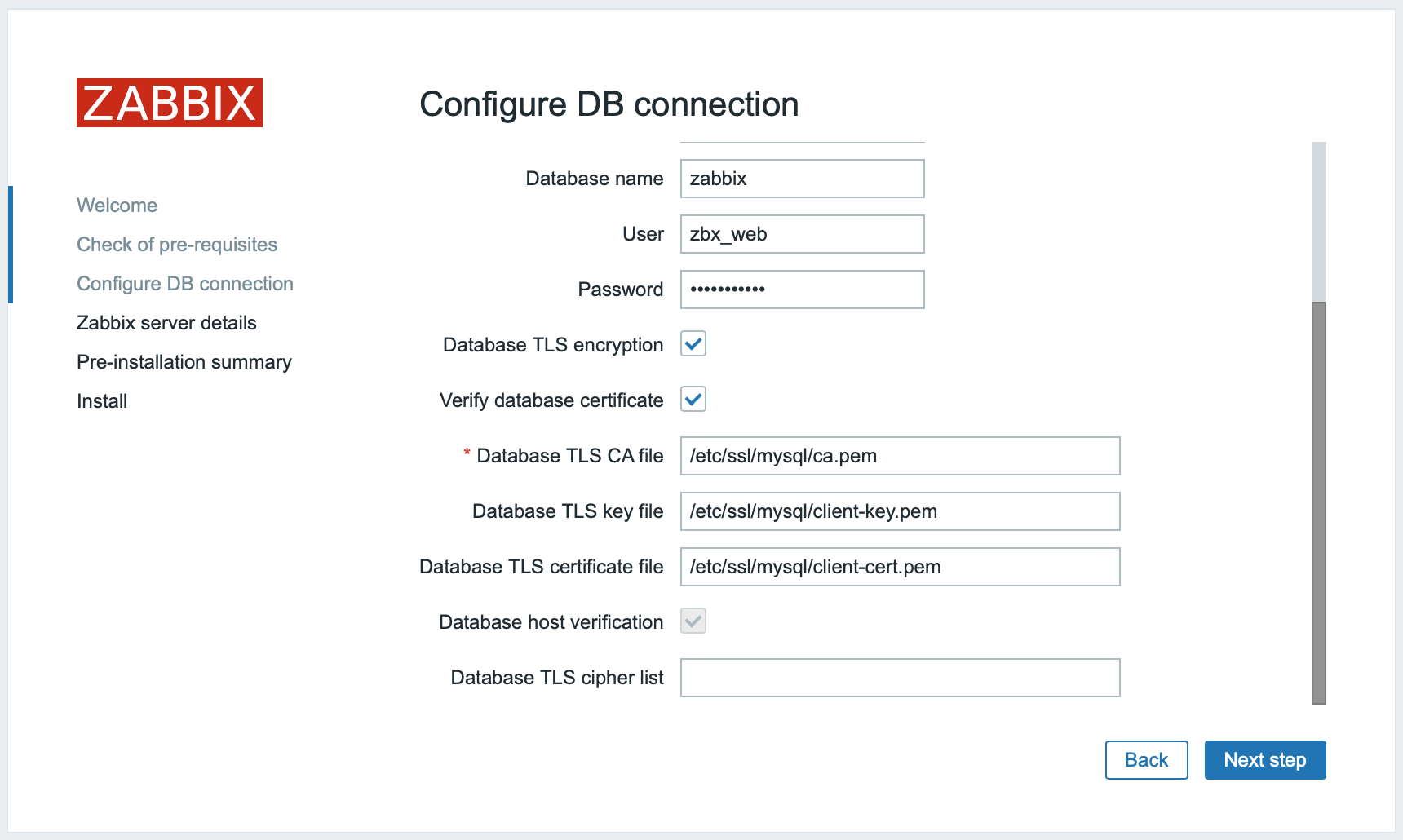
要为Zabbix前端与数据库之间的连接启用完全验证加密:
- 勾选数据库TLS加密和验证数据库证书
- 指定数据库TLS密钥file的路径
- 指定数据库TLS CAfile的路径
- 指定数据库TLS证书file的路径
注意数据库主机验证选项被勾选且显示为灰色 - 对于MySQL此步骤不可跳过.
如果数据库TLS加密套件列表字段留空,将启用前端(客户端)和服务器共同允许的通用加密套件. 或者,可以根据cipher configuration requirements明确设置加密套件.
或者,可以在/etc/zabbix/web/zabbix.conf.php中设置:
... // 用于TLS连接并严格定义加密套件列表. $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = '/etc/ssl/mysql/client-key.pem'; $DB['CERT_FILE'] = '/etc/ssl/mysql/client-cert.pem'; $DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem'; $DB['VERIFY_HOST'] = true; $DB['CIPHER_LIST'] = 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:TLS_AES_128_CCM_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-GC'; ... // 或 ... // 用于TLS连接且不定义加密套件列表 - 由MySQL服务器选择 $DB['ENCRYPTION'] = true; $DB['KEY_FILE'] = '/etc/ssl/mysql/client-key.pem'; $DB['CERT_FILE'] = '/etc/ssl/mysql/client-cert.pem'; $DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem'; $DB['VERIFY_HOST'] = true; $DB['CIPHER_LIST'] = ''; ...
Server
要为Zabbix server与数据库之间的连接启用完全验证加密,请配置 /etc/zabbix/zabbix_server.conf:
... DBHost=10.211.55.9 DBName=zabbix DBUser=zbx_srv DBPassword=<strong_password> DBTLSConnect=verify_full DBTLSCAFile=/etc/ssl/mysql/ca.pem DBTLSCertFile=/etc/ssl/mysql/client-cert.pem DBTLSKeyFile=/etc/ssl/mysql/client-key.pem ...

