1 configuração de criptografia MySQL
Visão geral
Esta seção fornece vários exemplos de configuração de criptografia para CentOS 8.2 e MySQL 8.0.21 e pode ser usada como um guia rápido para criptografar a conexão com o banco de dados.
Se o host MySQL estiver configurado como localhost, as opções de criptografia não estarão disponíveis. Nesse caso, a conexão entre o frontend do Zabbix e o banco de dados usa um arquivo de socket (no Unix) ou memória compartilhada (no Windows) e não pode ser criptografada.
A lista de combinações de criptografia não se limita às mencionadas nesta página. Existem muitas outras combinações disponíveis.
Pré-requisitos
Instale o banco de dados MySQL a partir do repositório oficial.
Para mais detalhes sobre como usar o repositório MySQL, consulte MySQL documentation.
O servidor MySQL está pronto para aceitar conexões seguras usando um certificado auto-assinado.
Para ver quais usuários estão usando uma conexão criptografada, execute a seguinte consulta (o Performance Schema deve estar ativado):
mysql> SELECT sbt.variable_value AS tls_version, t2.variable_value AS cipher, processlist_user AS user, processlist_host AS host
FROM performance_schema.status_by_thread AS sbt
JOIN performance_schema.threads AS t ON t.thread_id = sbt.thread_id
JOIN performance_schema.status_by_thread AS t2 ON t2.thread_id = t.thread_id
WHERE sbt.variable_name = 'Ssl_version' and t2.variable_name = 'Ssl_cipher'
ORDER BY tls_version;Modo obrigatório
Configuração do MySQL
Versões modernas do banco de dados estão prontas para 'modo de criptografia requerido' encryption mode. Um certificado do lado do servidor será criado após a configuração inicial e o lançamento.
Crie usuários e funções para os principais componentes:
mysql> CREATE USER
'zbx_srv'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>',
'zbx_web'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>'
REQUIRE SSL
PASSWORD HISTORY 5;
mysql> CREATE ROLE 'zbx_srv_role', 'zbx_web_role';
mysql> GRANT SELECT, UPDATE, DELETE, INSERT, CREATE, DROP, ALTER, INDEX, REFERENCES ON zabbix.* TO 'zbx_srv_role';
mysql> GRANT SELECT, UPDATE, DELETE, INSERT ON zabbix.* TO 'zbx_web_role';
mysql> GRANT 'zbx_srv_role' TO 'zbx_srv'@'%';
mysql> GRANT 'zbx_web_role' TO 'zbx_web'@'%';
mysql> SET DEFAULT ROLE 'zbx_srv_role' TO 'zbx_srv'@'%';
mysql> SET DEFAULT ROLE 'zbx_web_role' TO 'zbx_web'@'%';Observe que o protocolo X.509 não é utilizado para verificar a identidade, mas o usuário está configurado para usar apenas conexões criptografadas. Para mais detalhes sobre configuração de usuários, consulte MySQL documentation.
Execute para verificar a conexão (conexão via socket não pode ser usada para testar conexões seguras):
Verifique o status atual e as suítes de cifragem disponíveis:
mysql> status
--------------
mysql Ver 8.0.21 for Linux on x86_64 (MySQL Community Server - GPL)
Connection id: 62
Current database:
Current user: [email protected]
SSL: Cipher in use is TLS_AES_256_GCM_SHA384
mysql> SHOW SESSION STATUS LIKE 'Ssl_cipher_list'\G;
*************************** 1. row ***************************
Variable_name: Ssl_cipher_list
Value: TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:TLS_AES_128_CCM_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-DSS-AES128-SHA256:DHE-DSS-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-DSS-AES128-SHA:DHE-RSA-AES128-SHA:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES256-SHA:CAMELLIA256-SHA:CAMELLIA128-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA
1 row in set (0.00 sec)
ERROR:
No query specifiedFrontend
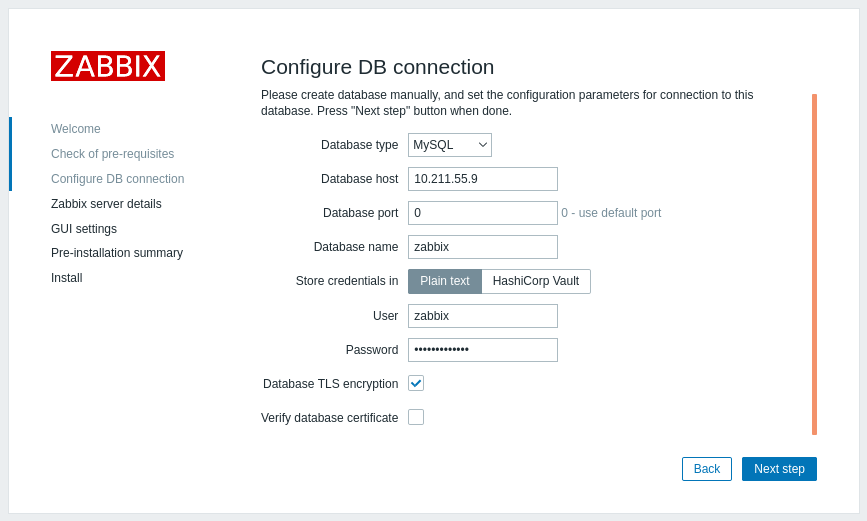
Para habilitar a criptografia de transporte apenas para conexões entre o frontend do Zabbix e o banco de dados:
- Marque Database TLS encryption
- Deixe Verify database certificate desmarcado
Servidor
Para habilitar a criptografia de transporte apenas para conexões entre o servidor e o banco de dados, configure /etc/zabbix/zabbix_server.conf:
...
DBHost=10.211.55.9
DBName=zabbix
DBUser=zbx_srv
DBPassword=<strong_password>
DBTLSConnect=required
...Verificar o modo CA
Copie o CA do MySQL necessário para o servidor frontend do Zabbix e atribua as permissões adequadas para permitir que o servidor web leia este arquivo.
O modo Verificar CA não funciona no SLES 12 e no RHEL 7 devido às bibliotecas mais antigas do MySQL.
Frontend
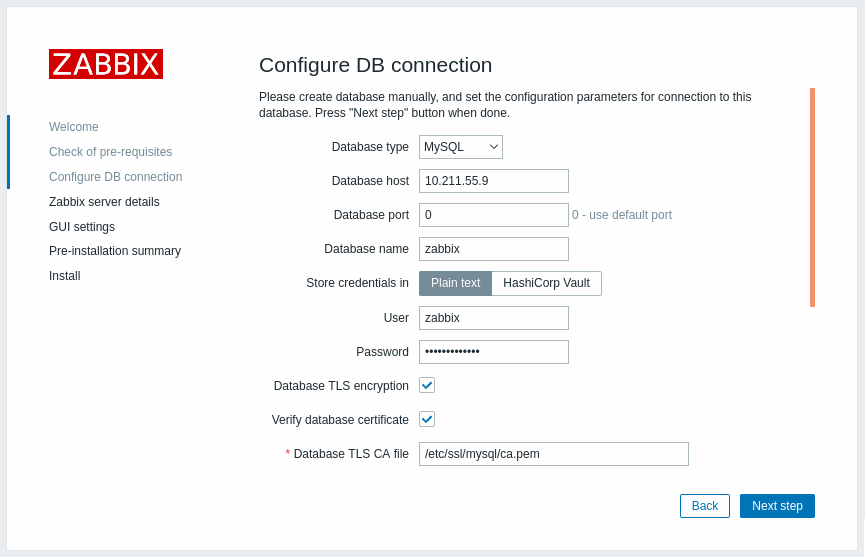
Para habilitar a criptografia com verificação de certificado para conexões entre o frontend do Zabbix e o banco de dados:
- Marque Database TLS encryption e Verify database certificate
- Especifique o caminho para o arquivo CA TLS do Banco de Dados
Alternativamente, isso pode ser configurado no arquivo /etc/zabbix/web/zabbix.conf.php:
...
$DB['ENCRYPTION'] = true;
$DB['KEY_FILE'] = '';
$DB['CERT_FILE'] = '';
$DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem';
$DB['VERIFY_HOST'] = false;
$DB['CIPHER_LIST'] = '';
...Solucione o problema do usuário usando a ferramenta de linha de comando para verificar se a conexão é possível para o usuário necessário:
Servidor
Para habilitar a criptografia com verificação de certificado para conexões entre o servidor Zabbix e o banco de dados, configure o arquivo /etc/zabbix/zabbix_server.conf:
...
DBHost=10.211.55.9
DBName=zabbix
DBUser=zbx_srv
DBPassword=<strong_password>
DBTLSConnect=verify_ca
DBTLSCAFile=/etc/ssl/mysql/ca.pem
...Verificar modo completo
Configuração MySQL
Defina a opção de configuração do servidor MySQL CE (/etc/my.cnf.d/server-tls.cnf) para:
[mysqld]
...
# in this examples keys are located in the MySQL CE datadir directory
ssl_ca=ca.pem
ssl_cert=server-cert.pem
ssl_key=server-key.pem
require_secure_transport=ON
tls_version=TLSv1.3
...As chaves para o servidor MySQL CE e o cliente (frontend do Zabbix) devem ser criadas manualmente de acordo com a documentação do MySQL CE: Creating SSL and RSA certificates and keys using MySQL ou Creating SSL certificates and keys using openssl
O certificado do servidor MySQL deve conter o campo Common Name definido para o nome FQDN, pois o frontend do Zabbix usará o nome DNS para se comunicar com o banco de dados ou o endereço IP do host do banco de dados.
Crie o usuário MySQL:
mysql> CREATE USER
'zbx_srv'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>',
'zbx_web'@'%' IDENTIFIED WITH mysql_native_password BY '<strong_password>'
REQUIRE X509
PASSWORD HISTORY 5;Verifique se é possível fazer login com esse usuário:
mysql -u zbx_web -p -h 10.211.55.9 --ssl-mode=VERIFY_IDENTITY --ssl-ca=/var/lib/mysql/ca.pem --ssl-cert=/var/lib/mysql/client-cert.pem --ssl-key=/var/lib/mysql/client-key.pemFrontend
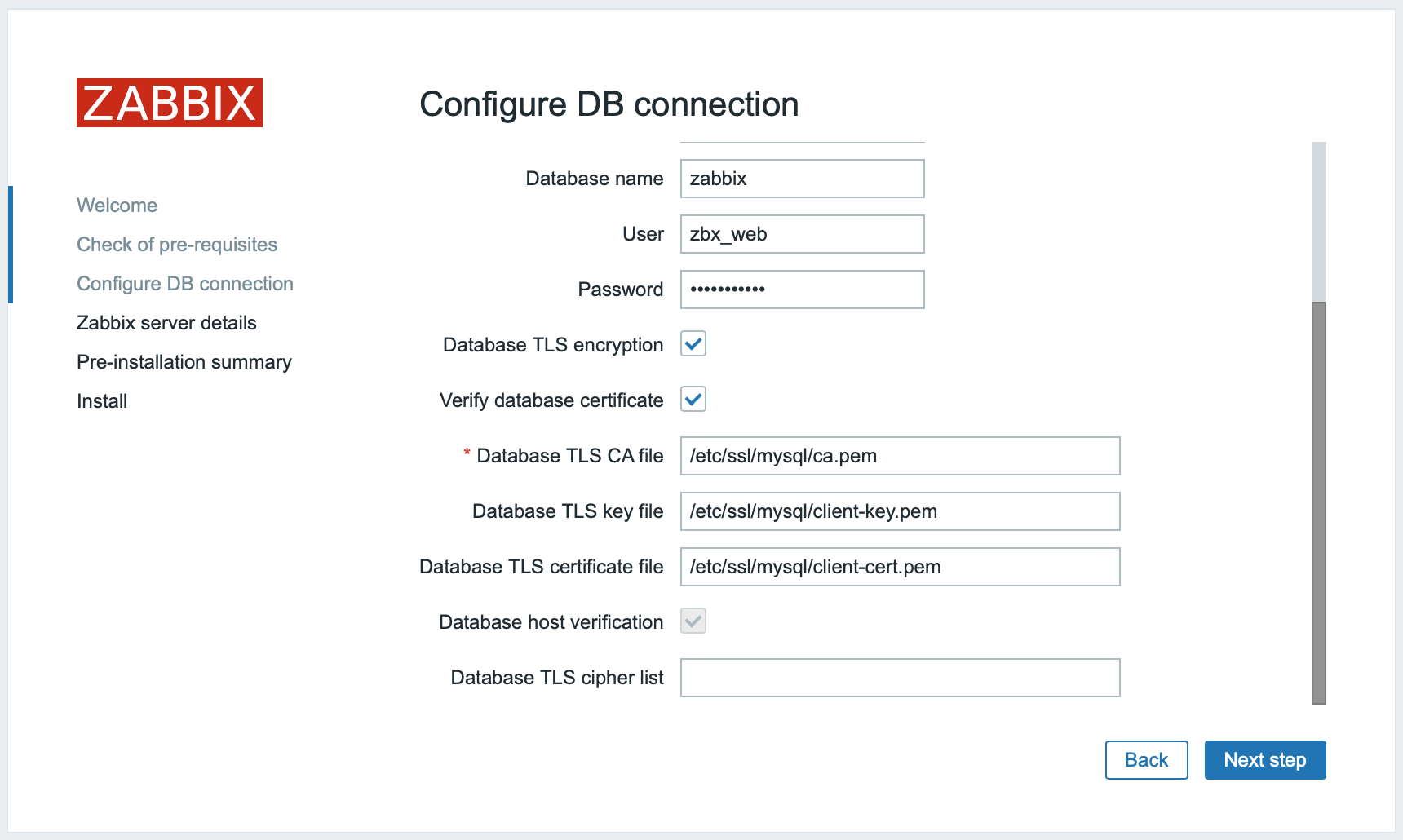
Para habilitar a criptografia com verificação completa para conexões entre o frontend do Zabbix e o banco de dados:
- Marque Criptografia TLS do Banco de Dados e Verificar certificado do banco de dados.
- Especifique o caminho para o arquivo da chave TLS do banco de dados
- Especifique o caminho para o arquivo CA TLS do banco de dados
- Especifique o caminho para o arquivo de certificado TLS do banco de dados
Observe que Verificação do host do banco de dados está marcada e desativada - esta etapa não pode ser ignorada para MySQL.
A lista de cifragem deve estar vazia, para que o frontend e o servidor possam negociar uma cifragem suportada por ambas as partes.
Alternativamente, isso pode ser configurado no arquivo /etc/zabbix/web/zabbix.conf.php:
...
// Usado para conexão TLS com lista de cifras estritamente definida.
$DB['ENCRYPTION'] = true;
$DB['KEY_FILE'] = '/etc/ssl/mysql/client-key.pem';
$DB['CERT_FILE'] = '/etc/ssl/mysql/client-cert.pem';
$DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem';
$DB['VERIFY_HOST'] = true;
$DB['CIPHER_LIST'] = 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:TLS_AES_128_CCM_SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-GC';
...
// ou
...
// Usado para conexão TLS sem lista de cifras definida - selecionada pelo servidor MySQL
$DB['ENCRYPTION'] = true;
$DB['KEY_FILE'] = '/etc/ssl/mysql/client-key.pem';
$DB['CERT_FILE'] = '/etc/ssl/mysql/client-cert.pem';
$DB['CA_FILE'] = '/etc/ssl/mysql/ca.pem';
$DB['VERIFY_HOST'] = true;
$DB['CIPHER_LIST'] = '';
...Servidor
Para habilitar a criptografia com verificação completa para conexões entre o servidor Zabbix e o banco de dados, configure o arquivo /etc/zabbix/zabbix_server.conf:

