Esta página inclui conteúdo traduzido automaticamente. Se você notar um erro, selecione-o e pressione Ctrl+Enter para reportá-lo aos editores.
14 Configuração do SAML com OneLogin
Visão geral
Esta seção fornece diretrizes para configurar o login único e o provisionamento de usuários no Zabbix a partir do OneLogin usando autenticação SAML 2.0.
Configuração do OneLogin
Criando o aplicativo
1. Faça login na sua conta no OneLogin. Para fins de teste, você pode criar uma conta de desenvolvedor gratuita no OneLogin.
2. Na interface web do OneLogin, navegue até Applications → Applications.
3. Clique em "Add App" e procure pelo aplicativo apropriado. As diretrizes nesta página são baseadas no exemplo do aplicativo SCIM Provisioner with SAML (SCIM v2 Enterprise, full SAML).
4. Para começar, você pode querer personalizar o nome de exibição do seu aplicativo. Você também pode adicionar o ícone e os detalhes do aplicativo. Depois disso, clique em Save.
Configurando o provisionamento SSO/SCIM
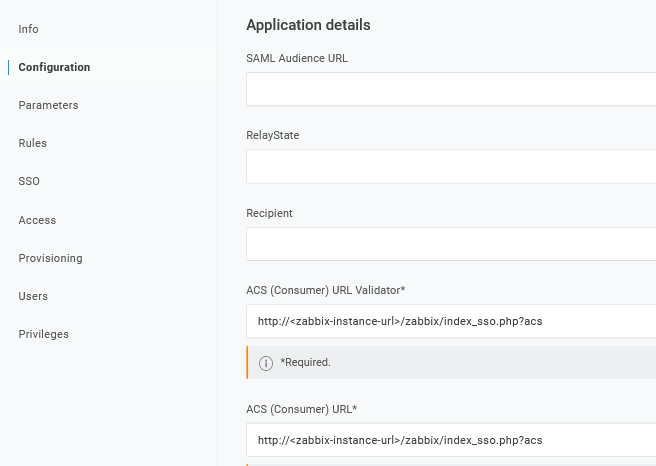
1. Em Configuration -> Application details, defina o endpoint de single sign-on do Zabbix http://<zabbix-instance-url>/zabbix/index_sso.php?acs como valor destes campos:
- ACS (Consumer) URL Validator
- ACS (Consumer) URL
Observe o uso de "http", e não "https", para que o parâmetro acs não seja cortado na requisição.
Também é possível usar "https". Para que isso funcione com o Zabbix, é necessário adicionar ao arquivo conf/zabbix.conf.php a seguinte linha:
$SSO['SETTINGS'] = ['use_proxy_headers' => true];Deixe as outras opções com seus valores padrão.
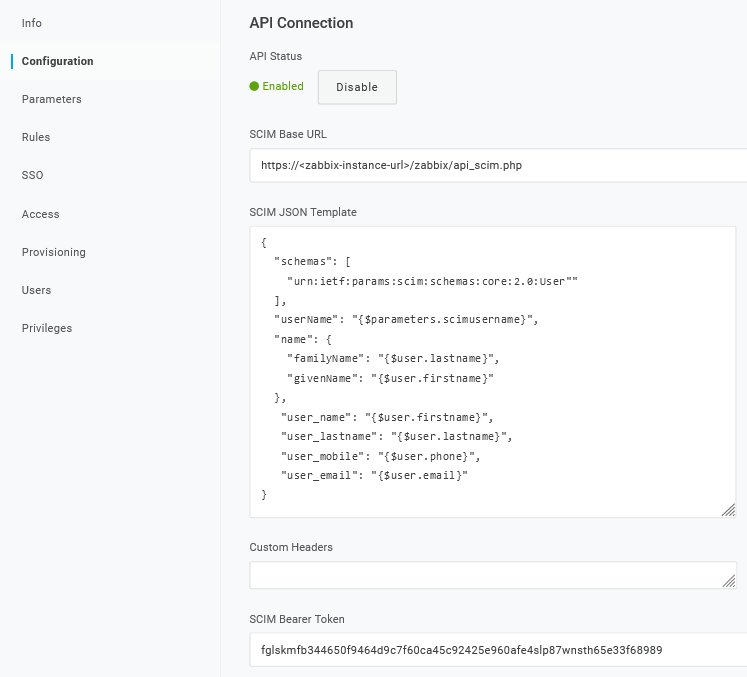
2. Em Configuration -> API connection, defina os seguintes valores:
- SCIM Base URL:
https://<zabbix-instance-url>/zabbix/api_scim.php - SCIM JSON Template: deve conter todos os atributos personalizados que você deseja passar para o Zabbix via SCIM, como
user_name,user_lastname,user_emaileuser_mobile:
{
"schemas": [
"urn:ietf:params:scim:schemas:core:2.0:User"
],
"userName": "{$parameters.scimusername}",
"name": {
"familyName": "{$user.lastname}",
"givenName": "{$user.firstname}"
},
"user_name": "{$user.firstname}",
"user_lastname": "{$user.lastname}",
"user_mobile": "{$user.phone}",
"user_email": "{$user.email}"
}Os nomes dos atributos são arbitrários. Podem ser usados nomes de atributos diferentes, porém, é necessário que correspondam ao respectivo valor do campo nas configurações SAML do Zabbix.
Observe que, para o provisionamento de usuários funcionar, o OneLogin precisa receber em resposta um atributo 'name' com 'givenName' e 'familyName', mesmo que não seja exigido pelo provedor de serviço. Assim, é necessário especificar isso no schema na parte de configuração do aplicativo.
- SCIM Bearer Token: insira um token de API do Zabbix com permissões de Super admin.
Clique em Enable para ativar a conexão.
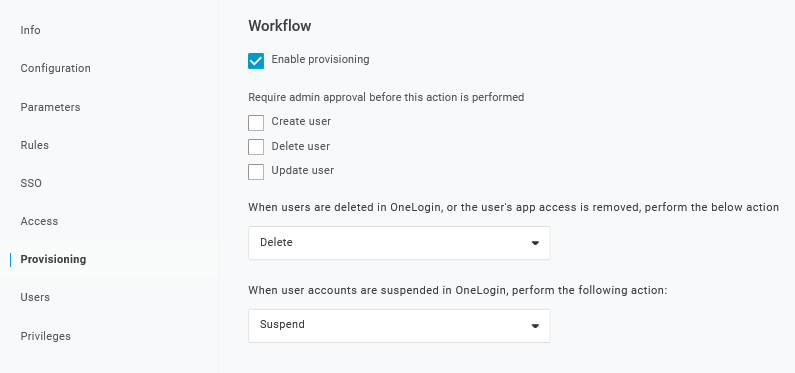
3. Na página Provisioning, habilite a opção Provisioning:
4. A página Parameters contém uma lista de parâmetros padrão:
- Certifique-se de que o 'scimusername' corresponda ao valor de login do usuário no OneLogin (por exemplo, e-mail);
- Marque a opção Include in User Provisioning para o parâmetro 'Groups';
- Clique em "+" para criar os parâmetros personalizados necessários para as asserções SAML e o provisionamento de usuários, como
user_name,user_lastname,user_emaileuser_mobile:
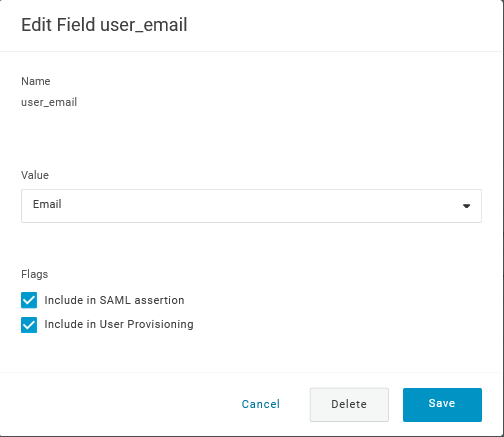
Ao adicionar um parâmetro, certifique-se de marcar as opções Include in SAML assertion e Include in User Provisioning.
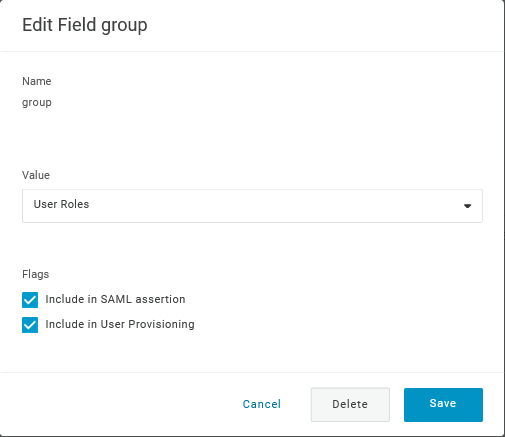
- Adicione um parâmetro 'group' que corresponda aos papéis de usuário no OneLogin. Os papéis de usuário serão passados como uma string, separados por ponto e vírgula
;. Os papéis de usuário do OneLogin serão usados para criar grupos de usuários no Zabbix:
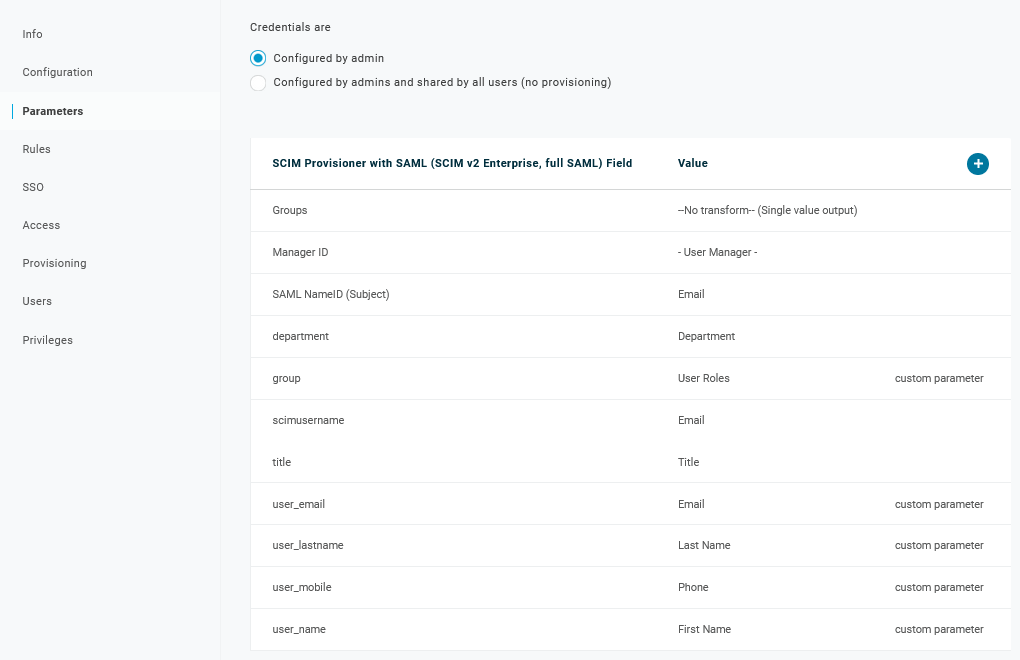
Verifique a lista de parâmetros:
5. Na página Rules, crie mapeamentos de papéis de usuário para o parâmetro padrão Groups.
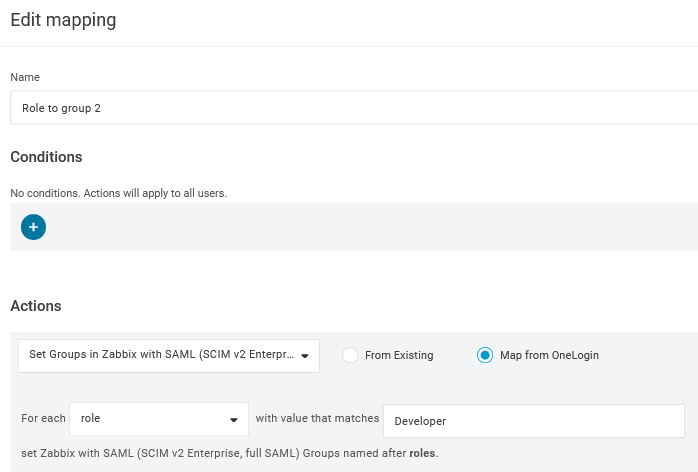
Você pode usar uma expressão regular para passar papéis específicos como grupos. Os nomes dos papéis não devem conter ;, pois o OneLogin o utiliza como separador ao enviar um atributo com vários papéis.
6. Baixe o certificado IdP. Defina as permissões 644 para ele executando:
Configuração do Zabbix
1. No Zabbix, acesse as configurações SAML e preencha as opções de configuração com base na configuração do OneLogin:
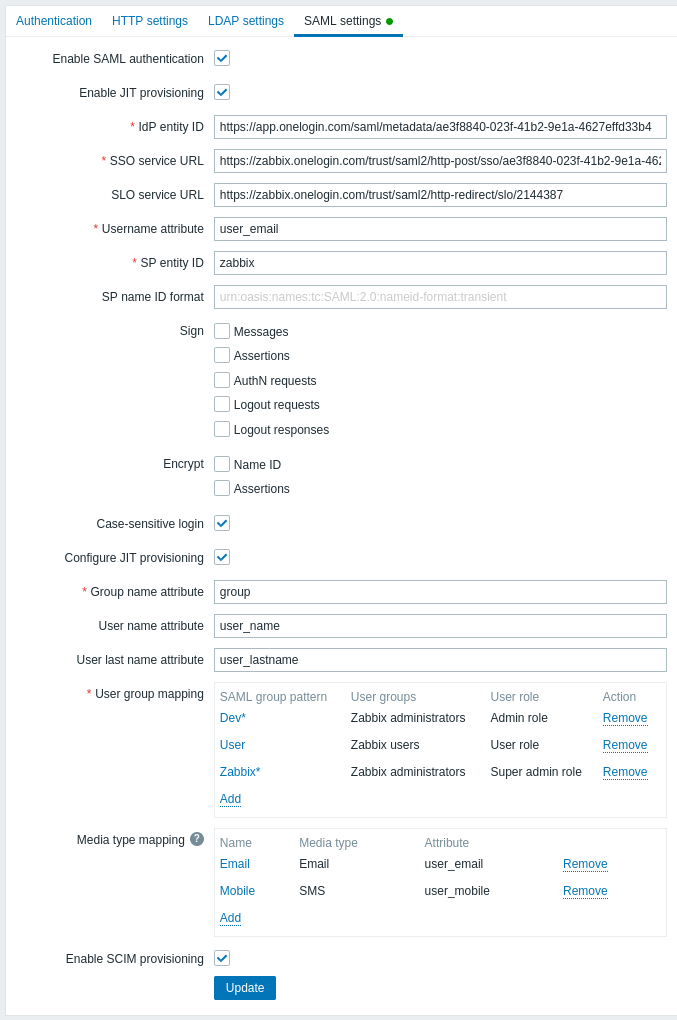
| Campo do Zabbix | Campo de configuração no OneLogin | Valor de exemplo |
|---|---|---|
| IdP entity ID | Issuer URL (veja a aba SSO do seu aplicativo no OneLogin) |
|
| SSO service URL | SAML 2.0 Endpoint (HTTP) (veja a aba SSO do seu aplicativo no OneLogin) |
|
| SLO service URL | SLO Endpoint (HTTP) (veja a aba SSO do seu aplicativo no OneLogin) |
|
| Username attribute | Parâmetro personalizado | user_email |
| Group name attribute | Parâmetro personalizado | group |
| User name attribute | Parâmetro personalizado | user_name |
| User last name attribute | Parâmetro personalizado | user_lastname |
Também é necessário configurar o mapeamento de grupos de usuários. O mapeamento de mídia é opcional. Clique em Atualizar para salvar essas configurações.
2. Adicione o certificado Base64 fornecido pelo OneLogin.
Se $SSO['CERT_STORAGE'] = 'database' estiver definido em zabbix.conf.php, você pode colar o texto do certificado ou fazer upload do arquivo do certificado no frontend durante a configuração do SAML — nenhum arquivo é necessário no sistema de arquivos.
Se $SSO['CERT_STORAGE'] = 'file' estiver definido em zabbix.conf.php, o certificado deve estar disponível no sistema de arquivos (por padrão em ui/conf/certs ou no caminho configurado em zabbix.conf.php) e o frontend não armazenará certificados no banco de dados. Observe que se $SSO['CERT_STORAGE'] não estiver definido ou estiver comentado, o armazenamento em arquivo é assumido e os certificados são lidos de ui/conf/certs.
Você pode acessar o download do certificado no OneLogin em Applications -> SSO -> clique em View details abaixo do certificado atual.
3. Pressione o botão Atualizar para salvar essas configurações.
Provisionamento de usuários SCIM
Com o provisionamento de usuários ativado, agora é possível adicionar/atualizar usuários e seus papéis no OneLogin e tê-los imediatamente provisionados no Zabbix.
Por exemplo, você pode criar um novo usuário:
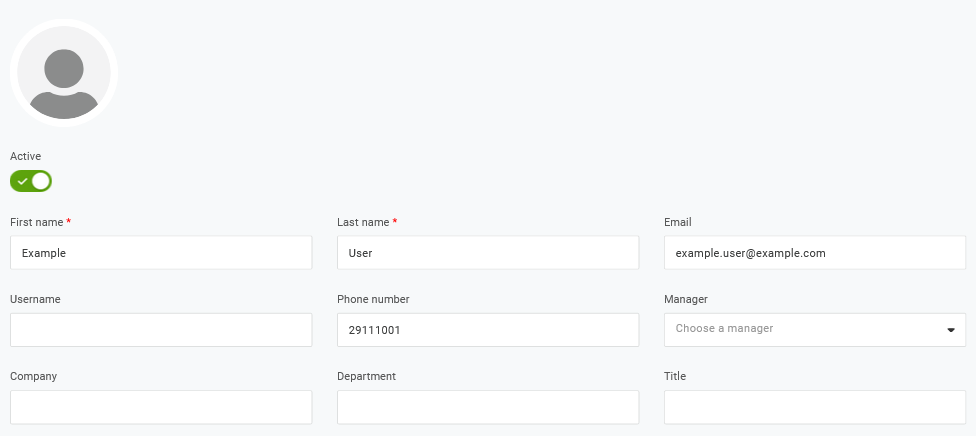
Adicione-o a um papel de usuário e ao aplicativo que irá provisionar o usuário:
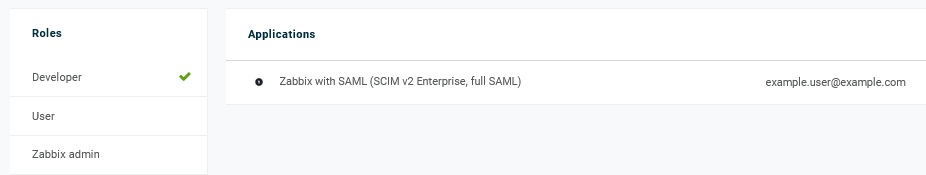
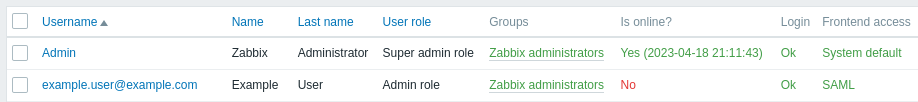
Ao salvar o usuário, ele será provisionado para o Zabbix. Em Aplicativo -> Usuários, você pode verificar o status de provisionamento dos usuários atuais do aplicativo:
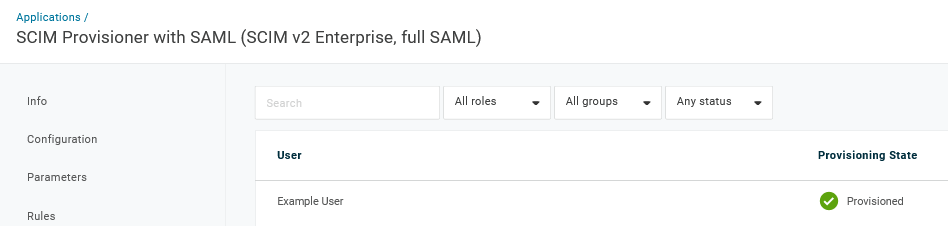
Se for provisionado com sucesso, o usuário poderá ser visto na lista de usuários do Zabbix.