13 OneLoginを使用したSAMLセットアップ
概要
このセクションでは、SAML 2.0 認証を使用して OneLogin から Zabbix へのシングルサインオンとユーザープロビジョニングを構成するためのガイドラインを示します。
OneLoginの設定
アプリケーションの作成
1. OneLogin のアカウントにログインします。テスト目的で、OneLogin で無料の開発者アカウントを作成できます。
2. OneLogin の Web インターフェースで、"アプリケーション"→"アプリケーション" に移動します。
3. "アプリを追加"をクリックし、適切なアプリを検索します。このページのガイドラインは、SCIM Provisioner with SAML (SCIM v2 Enterprise, full SAML) アプリの例に基づいています。
4. まず、アプリの表示名をカスタマイズします。アイコンやアプリの詳細を追加することもできます。その後、保存をクリックします。
Setting up SSO/SCIM provisioning
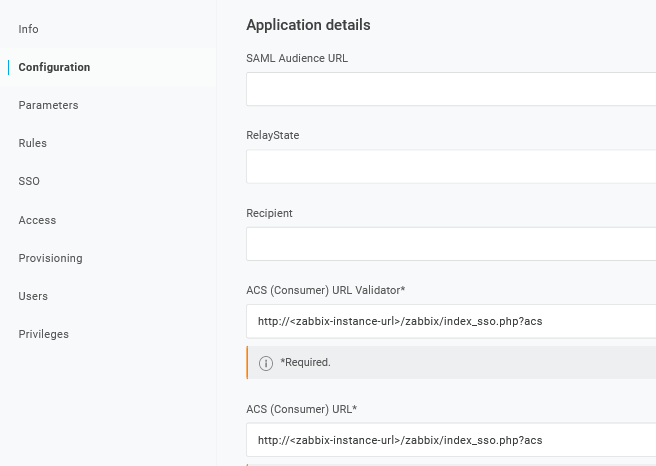
1. In Configuration -> Application details, set the Zabbix single sign-on endpoint http://<zabbix-instance-url>/zabbix/index_sso.php?acs as the value of these fields:
- ACS (Consumer) URL Validator
- ACS (Consumer) URL
Note the use of "http", and not "https", so that the acs parameter is not cut out in the request.
It is also possible to use "https". To make that work with Zabbix, it is necessary to add to conf/zabbix.conf.php the following line:
$SSO['SETTINGS'] = ['use_proxy_headers' => true];Leave other options with their default values.
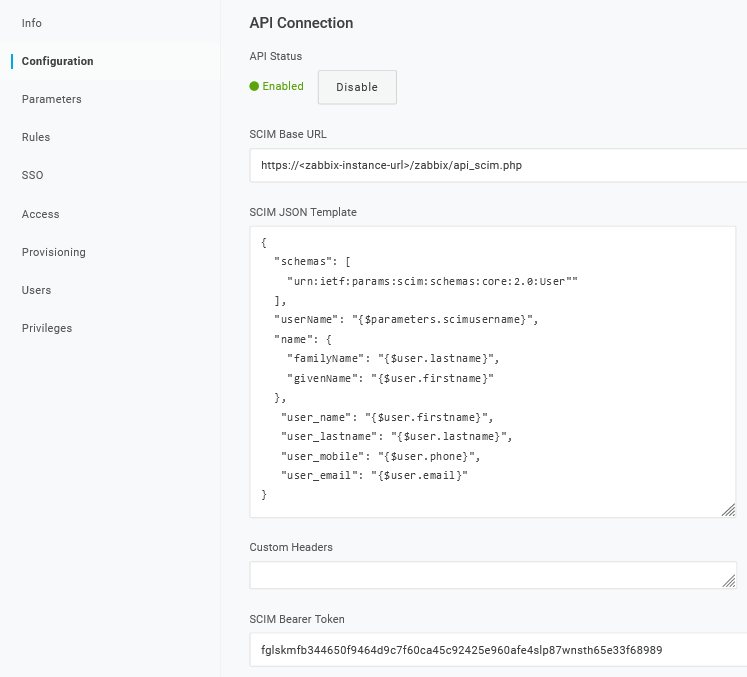
2. In Configuration -> API connection, set the following values:
- SCIM Base URL:
https://<zabbix-instance-url>/zabbix/api_scim.php - SCIM JSON Template: should contain all custom attributes that you would like to pass to Zabbix via SCIM such as
user_name,user_lastname,user_email, anduser_mobile:
{
"schemas": [
"urn:ietf:params:scim:schemas:core:2.0:User"
],
"userName": "{$parameters.scimusername}",
"name": {
"familyName": "{$user.lastname}",
"givenName": "{$user.firstname}"
},
"user_name": "{$user.firstname}",
"user_lastname": "{$user.lastname}",
"user_mobile": "{$user.phone}",
"user_email": "{$user.email}"
}The attribute names are arbitrary. Different attribute names may be used, however, it is required that they match the respective field value in Zabbix SAML settings.
Note that for user provisioning to work, OneLogin needs to receive in response a 'name' attribute with 'givenName' and 'familyName', even if it was not required by the service provider. Thus it is necessary to specify this in the schema in the application configuration part.
- SCIM Bearer Token: enter a Zabbix API token with Super admin permissions.
Click on Enable to activate the connection.
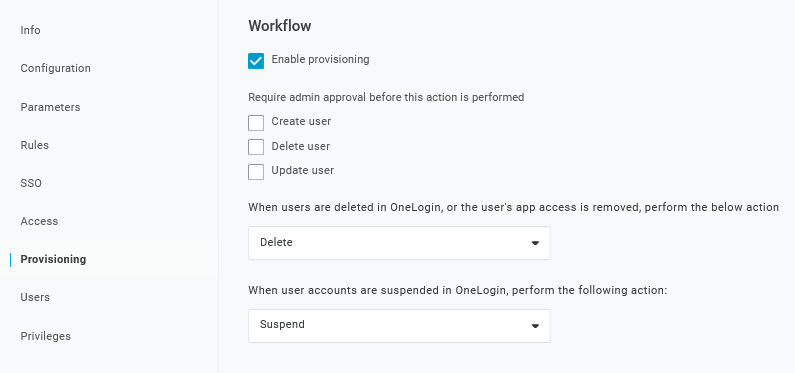
3. In the Provisioning page, enable the Provisioning option:
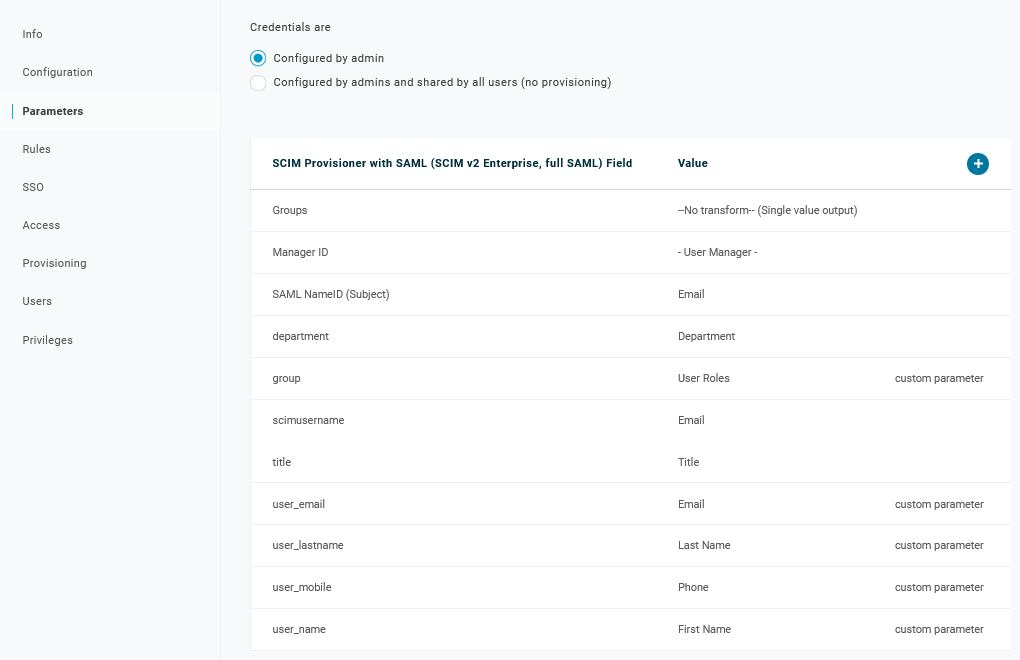
4. The Parameters page contains a list of default parameters:
- Make sure that the 'scimusername' matches the user login value in OneLogin (e.g. email);
- Mark the Include in User Provisioning option for the 'Groups' parameter;
- Click on "+" to create the custom parameters that are required for SAML assertions and user provisioning such as
user_name,user_lastname,user_email, anduser_mobile:
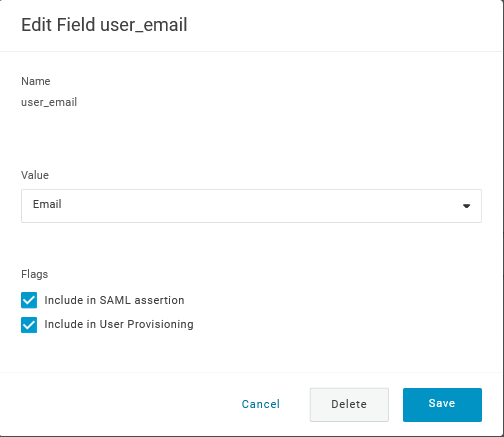
When adding a parameter, make sure to mark both the Include in SAML assertion and Include in User Provisioning options.
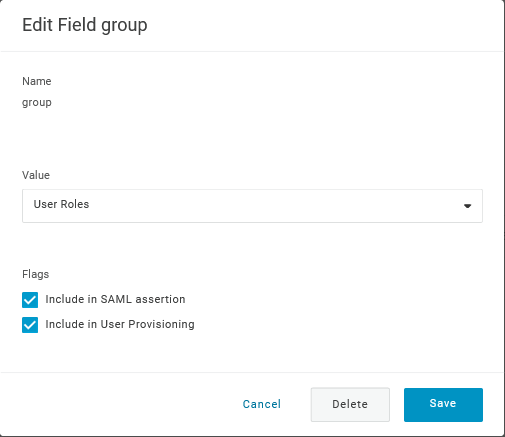
- Add a 'group' parameter that matches user roles in OneLogin. User roles will be passed as a string, separated by a semicolon
;. The OneLogin user roles will be the used for creating user groups in Zabbix:
Verify the list of parameters:
5. In the Rules page, create user role mappings to the default Groups parameter.
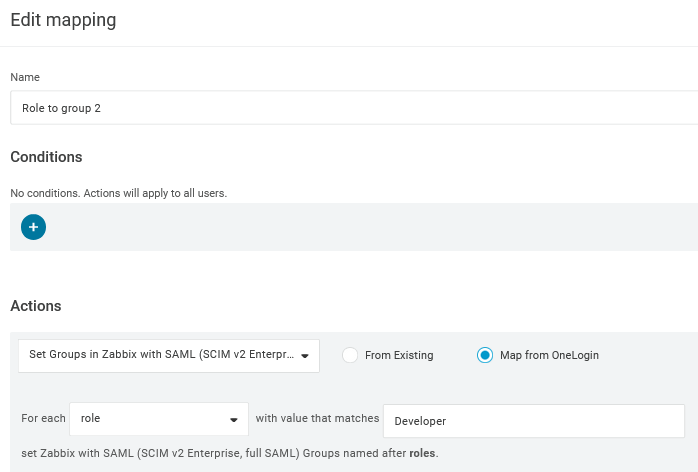
You may use a regular expression to pass specific roles as groups. The role names should not contain ; as OneLogin uses it as a separator when sending an attribute with several roles.
Zabbix configuration
1. In Zabbix, go to the SAML settings and fill the configuration options based on the OneLogin configuration:
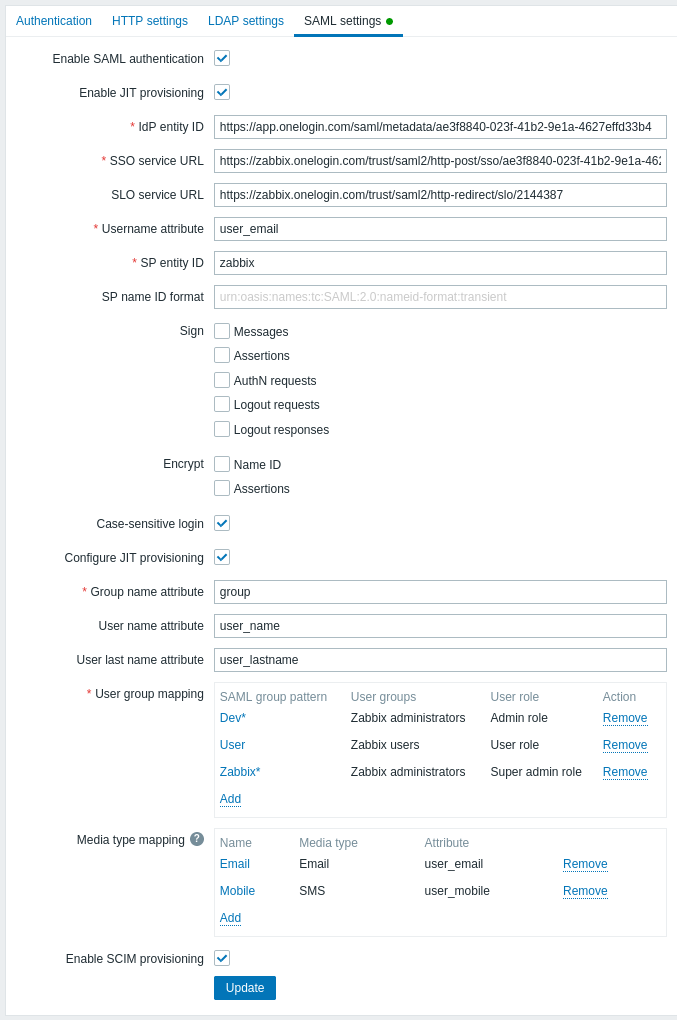
| Zabbix field | Setup field in OneLogin | Sample value |
|---|---|---|
| IdP entity ID | Issuer URL (see SSO tab of your application in OneLogin) |
|
| SSO service URL | SAML 2.0 Endpoint (HTTP) (see SSO tab of your application in OneLogin) |
|
| SLO service URL | SLO Endpoint (HTTP) (see SSO tab of your application in OneLogin) |
|
| Username attribute | Custom parameter | user_email |
| Group name attribute | Custom parameter | group |
| User name attribute | Custom parameter | user_name |
| User last name attribute | Custom parameter | user_lastname |
It is also required to configure user group mapping. Media mapping is optional. Click on Update to save these settings.
2. Download the certificate provided by OneLogin and place it into conf/certs of the Zabbix frontend installation, as idp.crt.
Set 644 permissions to it by running:
You can access the certificate download in OneLogin in Applications -> SSO -> click on View details under the current certificate.
It is possible to use a different certificate name and location. In that case, make sure to add to conf/zabbix.conf.php the following line:
$SSO['IDP_CERT'] = 'path/to/certname.crt';SCIM ユーザープロビジョニング
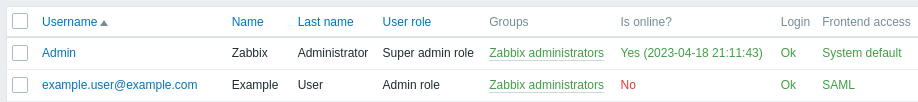
ユーザープロビジョニングを有効にすると、OneLogin でユーザーとそのロールを追加/更新し、Zabbix にすぐにプロビジョニングできるようになります。
例えば、新しいユーザーを作成します。
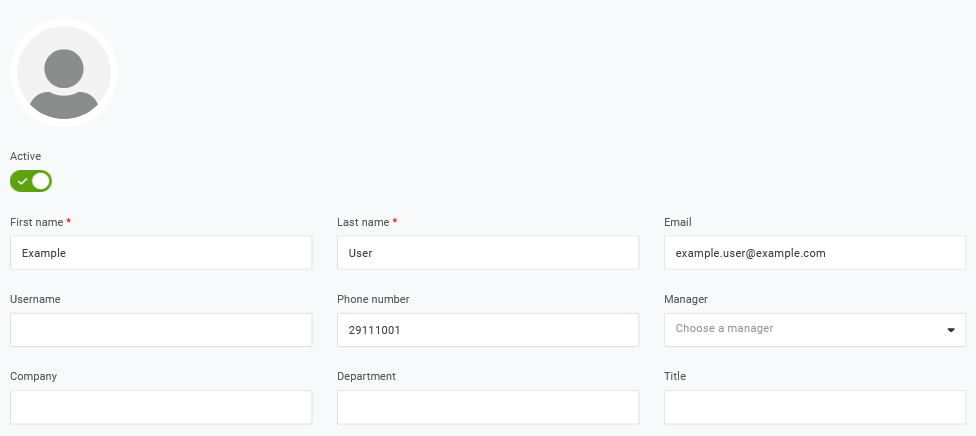
ユーザーロールと、ユーザーをプロビジョニングするアプリケーションを追加します。
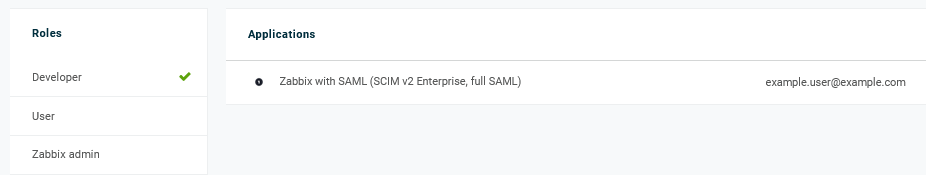
ユーザーを保存すると、Zabbix にプロビジョニングされます。 アプリケーション → ユーザー で、現在のアプリケーションユーザーのプロビジョニングステータスを確認できます。
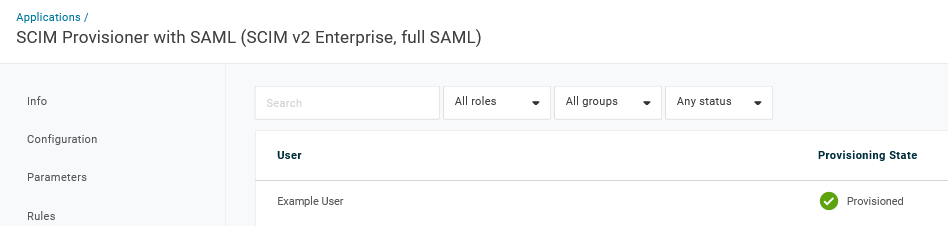
プロビジョニングが正常に完了すると、Zabbix ユーザーリストにユーザーが表示されます。